DNA Center - PnP - What It Does To Your Devices
Table of Contents
DNA Center is a management platform that enables users to bring automation to their network. It also offers an assurance feature that aids in troubleshooting and ensuring the network runs as it should using 360 views with health status of network, client, and apps. The latter will not be in focus for this post. Rather a closer look at what DNAC actually does to your devices in regards to configuration will be revealed.
Similar posts exist:
DNA Center - Provision - What It Does To Your Devices DNA Center - Discovery - What It Does To Your Devices
In this post I’m using DNAC version 1.3.1.4.
Test Case
One simple test case is all we need to see what DNAC does:
- Onboard a 2960X using PnP with a simple template
- Investigate the CLI commands pushed by DNAC to the device
Topology
The below topology is used for this post:
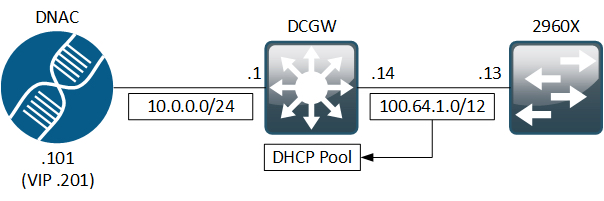
DCGW is the L3 switch routing between the two connected networks. It has a DHCP pool defined for Vlan1 where the 2960X is connected:
! DCGW DHCP Pool for PnP:
ip dhcp excluded-address 100.64.1.14
!
ip dhcp pool dhcp_vlan1
network 100.64.1.12 255.255.255.252
default-router 100.64.1.14
option 43 ascii 5A1D;B2;K4;I10.0.0.201;J80;
As you can see I like to use the RFC 6598 address space. As of DNAC version 1.2.8 you can also use these addresses for the Services Subnet and Cluster Services Subnet. See the Required IP Addresses and Subnets section of the Plan the Deployment headline in the Install and Upgrade Guides
PnP
I’ve previously written a post about PnP and a revisit of the feature in the PnP Revisited post.
The focus now is to see exactly what DNAC does to your switch upon onboarding using this simple template:
hostname 2960X_PnP-TEST
!
event manager applet catchall
event cli pattern ".*" sync no skip no
action 1 syslog msg "$_cli_msg"
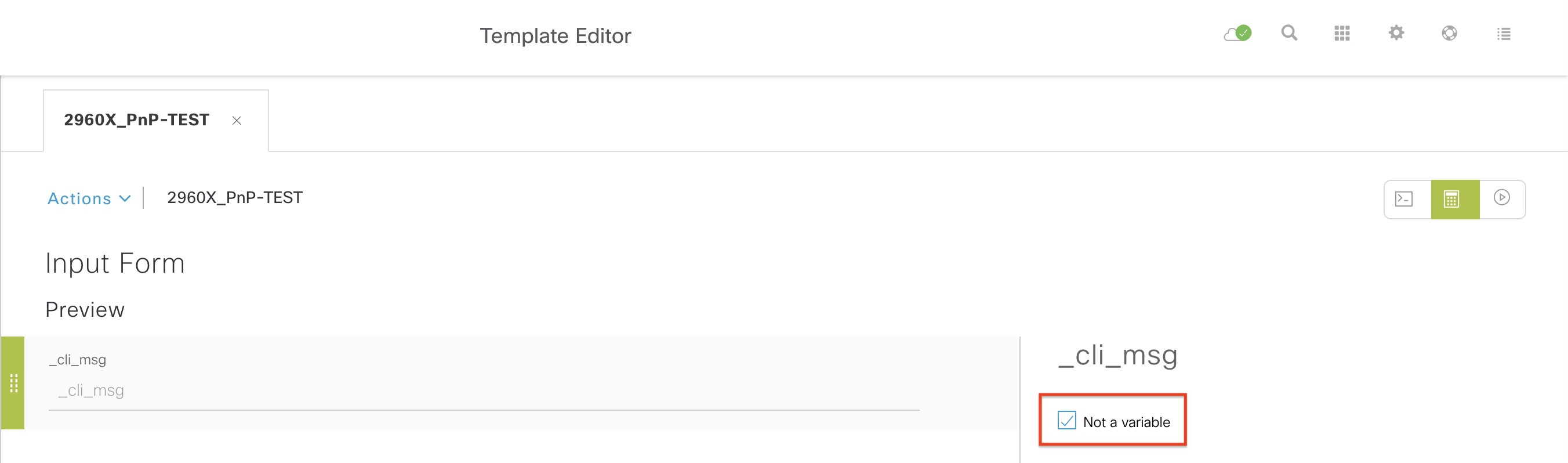
The EEM applet logs everything that is entered into the device on the CLI. This way we can monitor what DNAC configures right after the template has been implemented. A very useful feature in troubleshooting as well.
The sync no tells the applet to run the command asynchronously (not wait until the applet is finished) and skip no to execute the command. The variable $_cli_msg holds the actual command entered. Using $ like this in our template will not work without telling DNAC that it isn’t a variable requiring user input:
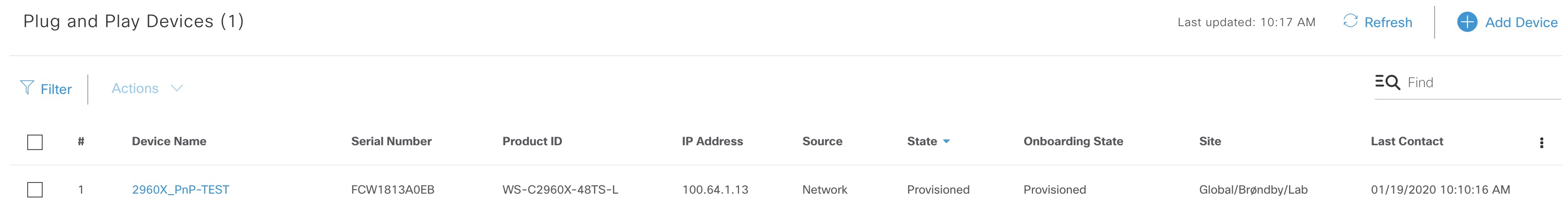
After the 2960X boots it receives the IP address 100.64.1.13 along with option 43 that instructs it to contact DNAC for PnP onboarding. It will show up as Unclaimed - Initialized in the PnP app. I claim the device using the above template and upon successful provisioning the state is this:
Onboarding Commands
Now let’s have a look at what happened on the console during the provisioning:
Press RETURN to get started!
*Mar 1 00:00:18.042: Read env variable - LICENSE_BOOT_LEVEL =
*Jan 2 00:00:00.153: %IOS_LICENSE_IMAGE_APPLICATION-6-LICENSE_LEVEL: Module name = c2960x_lanbase Next reboot level = lanbase and License = lanbase
Jan 19 09:02:38.123: in Switch 0. Cannot read pid from Flexstack module
Jan 19 09:03:21.849: %STACKMGR-4-SWITCH_ADDED: Switch 1 has been ADDED to the stack
Jan 19 09:03:23.222: %LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan1, changed state to down
Jan 19 09:03:23.222: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0, changed state to down
Jan 19 09:03:28.161: %SPANTREE-5-EXTENDED_SYSID: Extended SysId enabled for type vlan
Jan 19 09:03:51.286: %STACKMGR-5-SWITCH_READY: Switch 1 is READY
Jan 19 09:03:51.286: %STACKMGR-4-STACK_LINK_CHANGE: Stack Port 1 Switch 1 has changed to state DOWN
Jan 19 09:03:51.286: %STACKMGR-4-STACK_LINK_CHANGE: Stack Port 2 Switch 1 has changed to state DOWN
Jan 19 09:03:51.891: %STACKMGR-5-MASTER_READY: Master Switch 1 is READY
Jan 19 09:03:52.030: %SYS-5-RESTART: System restarted --
Cisco IOS Software, C2960X Software (C2960X-UNIVERSALK9-M), Version 15.2(7)E1, RELEASE SOFTWARE (fc4)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2019 by Cisco Systems, Inc.
Compiled Sat 07-Dec-19 09:42 by prod_rel_team
Jan 19 09:03:53.292: %USB_CONSOLE-6-MEDIA_RJ45: Console media-type is RJ45.
Jan 19 09:03:54.012: %LINK-3-UPDOWN: Interface FastEthernet0, changed state to down
Jan 19 09:03:54.722: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet1/0/48, changed state to up
Jan 19 09:03:55.015: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0, changed state to down
Jan 19 09:03:56.721: %LINK-3-UPDOWN: Interface GigabitEthernet1/0/48, changed state to up
Jan 19 09:03:57.721: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet1/0/48, changed state to down
Jan 19 09:03:57.787: %LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan1, changed state to up
Jan 19 09:03:58.780: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet1/0/48, changed state to up
Jan 19 09:04:04.016: %PNPA-DHCP Op-43 Msg: Process state = READY
Jan 19 09:04:04.016: %PNPA-DHCP Op-43 Msg: OK to process message
Jan 19 09:04:04.019: XML-UPDOWN: PNPA_DHCP_OP43 XML Interface(102) UP. PID=93
Jan 19 09:04:04.019: %PNPA-DHCP Op-43 Msg: _pdoon.1.ntf.don=93
Jan 19 09:04:04.019: %PNPA-DHCP Op-43 Msg: _pdoop.1.org=[A1D;B2;K4;I10.0.0.201;J80;]
Jan 19 09:04:04.019: %PNPA-DHCP Op-43 Msg: _pdgfa.1.inp=[B2;K4;I10.0.0.201;J80;]
Jan 19 09:04:04.019: %PNPA-DHCP Op-43 Msg: _pdgfa.1.B2.s12=[ ipv4 ]
Jan 19 09:04:04.019: %PNPA-DHCP Op-43 Msg: _pdgfa.1.K4.htp=[ transport http ]
Jan 19 09:04:04.019: %PNPA-DHCP Op-43 Msg: _pdgfa.1.Ix.srv.ip.rm=[ 10.0.0.201 ]
Jan 19 09:04:04.019: %PNPA-DHCP Op-43 Msg: _pdgfa.1.Jx.srv.rt.rm=[ port 80 ]
Jan 19 09:04:04.019: %PNPA-DHCP Op-43 Msg: _pdoop.1.ztp=[pnp-zero-touch] host=[] ipad=[10.0.0.201] port=80
Jan 19 09:04:04.019: %PNPA-DHCP Op-43 Msg: _pors.done=1
Jan 19 09:04:04.019: %PNPA-DHCP Op-43 Msg: _pdokp.1.kil=[PNPA_DHCP_OP43] pid=93 idn=[Vlan1]
Jan 19 09:04:04.019: XML-UPDOWN: Vlan1 XML Interface(102) SHUTDOWN(101). PID=93
Jan 19 09:04:18.011: %PNP-6-HTTP_CONNECTING: PnP Discovery trying to connect to PnP server http://10.0.0.201:80/pnp/HELLO
Jan 19 09:04:19.017: %PNP-6-HTTP_CONNECTED: PnP Discovery connected to PnP server http://10.0.0.201:80/pnp/HELLO
Jan 19 09:04:20.027: %PNP-6-PROFILE_CONFIG: PnP Discovery profile pnp-zero-touch configured
Jan 19 09:05:08.419: %PNP-6-PNP_DISCOVERY_DONE: PnP Discovery done successfully
Jan 19 09:05:09.289: %SYS-6-CLOCKUPDATE: System clock has been updated from 09:05:04 UTC Sun Jan 19 2020 to 09:05:09 UTC Sun Jan 19 2020, configured from console by console.
Jan 19 09:05:09.537: %PKI-4-NOCONFIGAUTOSAVE: Configuration was modified. Issue "write memory" to save new IOS PKI configuration
000041: Jan 19 09:09:13.045: %SSH-5-ENABLED: SSH 1.99 has been enabled
000042: Jan 19 09:09:13.331: Configuring snmpv3 USM user, persisting snmpEngineBoots. Please Wait...
000043: Jan 19 09:09:13.541: %PARSER-4-BADCFG: Unexpected end of configuration file.
000044: Jan 19 09:09:24.030: %HA_EM-6-LOG: catchall: show ip interface brief
000045: Jan 19 09:09:29.186: %HA_EM-6-LOG: catchall: show ipv6 interface brief
000046: Jan 19 09:09:34.401: %HA_EM-6-LOG: catchall: copy running-config startup-config
000047: Jan 19 09:09:45.201: %HA_EM-6-LOG: catchall: enable
000048: Jan 19 09:09:45.226: %HA_EM-6-LOG: catchall: terminal length 0
000049: Jan 19 09:09:45.257: %HA_EM-6-LOG: catchall: terminal width 0
000050: Jan 19 09:09:45.306: %HA_EM-6-LOG: catchall: show running-config
000051: Jan 19 09:09:46.375: %HA_EM-6-LOG: catchall: show auto qos
000052: Jan 19 09:09:46.498: %HA_EM-6-LOG: catchall: show sdm prefer
000053: Jan 19 09:09:46.578: %HA_EM-6-LOG: catchall: show mls qos queue-set
000054: Jan 19 09:09:46.865: %HA_EM-6-LOG: catchall: show ip route summary
000055: Jan 19 09:09:46.945: %HA_EM-6-LOG: catchall: show flow monitor
000056: Jan 19 09:09:47.061: %HA_EM-6-LOG: catchall: show interfaces
000057: Jan 19 09:09:47.504: %HA_EM-6-LOG: catchall: show version
000058: Jan 19 09:09:47.990: %HA_EM-6-LOG: catchall: show ip ospf
000059: Jan 19 09:09:48.029: %HA_EM-6-LOG: catchall: show ospfv3
000060: Jan 19 09:09:48.067: %HA_EM-6-LOG: catchall: show ospfv3 interface
000061: Jan 19 09:09:48.179: %HA_EM-6-LOG: catchall: show standby
000062: Jan 19 09:09:48.224: %HA_EM-6-LOG: catchall: show cef state
000063: Jan 19 09:09:48.368: %HA_EM-6-LOG: catchall: show cdp neighbors detail
000064: Jan 19 09:09:48.420: %HA_EM-6-LOG: catchall: show lldp neighbors
000065: Jan 19 09:09:48.487: %HA_EM-6-LOG: catchall: show ip device tracking all
000066: Jan 19 09:09:48.536: %HA_EM-6-LOG: catchall: show arp
000067: Jan 19 09:09:48.598: %HA_EM-6-LOG: catchall: show mac address-table
000068: Jan 19 09:09:48.700: %HA_EM-6-LOG: catchall: show interfaces switchport
000069: Jan 19 09:09:49.039: %HA_EM-6-LOG: catchall: show lldp neighbors detail
000070: Jan 19 09:09:49.140: %HA_EM-6-LOG: catchall: show flow monitor
000071: Jan 19 09:09:49.189: %HA_EM-6-LOG: catchall: show logging
000072: Jan 19 09:09:49.249: %HA_EM-6-LOG: catchall: show snmp
000073: Jan 19 09:09:49.294: %HA_EM-6-LOG: catchall: show snmp host
000074: Jan 19 09:09:49.367: %HA_EM-6-LOG: catchall: show cef interface brief
000075: Jan 19 09:09:49.539: %HA_EM-6-LOG: catchall: show clock
000076: Jan 19 09:09:49.734: %HA_EM-6-LOG: catchall: show license right-to-use detail
000077: Jan 19 09:09:49.979: %HA_EM-6-LOG: catchall: show license right-to-use usage
000078: Jan 19 09:09:50.203: %HA_EM-6-LOG: catchall: show license right-to-use summary
000079: Jan 19 09:09:50.395: %HA_EM-6-LOG: catchall: show hosts
000080: Jan 19 09:09:50.912: %HA_EM-6-LOG: catchall: show ip access-lists
000081: Jan 19 09:09:50.954: %HA_EM-6-LOG: catchall: show ipv6 access-list
000082: Jan 19 09:09:51.405: %HA_EM-6-LOG: catchall: show template
000083: Jan 19 09:09:51.587: %HA_EM-6-LOG: catchall: show template interface source built-in AP_INTERFACE_TEMPLATE
000084: Jan 19 09:09:51.664: %HA_EM-6-LOG: catchall: show template interface binding AP_INTERFACE_TEMPLATE
000085: Jan 19 09:09:51.751: %HA_EM-6-LOG: catchall: show template interface source built-in DMP_INTERFACE_TEMPLATE
000086: Jan 19 09:09:51.828: %HA_EM-6-LOG: catchall: show template interface binding DMP_INTERFACE_TEMPLATE
000087: Jan 19 09:09:51.919: %HA_EM-6-LOG: catchall: show template interface source built-in IP_CAMERA_INTERFACE_TEMPLATE
000088: Jan 19 09:09:51.999: %HA_EM-6-LOG: catchall: show template interface binding IP_CAMERA_INTERFACE_TEMPLATE
000089: Jan 19 09:09:52.094: %HA_EM-6-LOG: catchall: show template interface source built-in IP_PHONE_INTERFACE_TEMPLATE
000090: Jan 19 09:09:52.174: %HA_EM-6-LOG: catchall: show template interface binding IP_PHONE_INTERFACE_TEMPLATE
000091: Jan 19 09:09:52.293: %HA_EM-6-LOG: catchall: show template interface source built-in LAP_INTERFACE_TEMPLATE
000092: Jan 19 09:09:52.366: %HA_EM-6-LOG: catchall: show template interface binding LAP_INTERFACE_TEMPLATE
000093: Jan 19 09:09:52.468: %HA_EM-6-LOG: catchall: show template interface source built-in MSP_CAMERA_INTERFACE_TEMPLATE
000094: Jan 19 09:09:52.548: %HA_EM-6-LOG: catchall: show template interface binding MSP_CAMERA_INTERFACE_TEMPLATE
000095: Jan 19 09:09:52.639: %HA_EM-6-LOG: catchall: show template interface source built-in MSP_VC_INTERFACE_TEMPLATE
000096: Jan 19 09:09:52.712: %HA_EM-6-LOG: catchall: show template interface binding MSP_VC_INTERFACE_TEMPLATE
000097: Jan 19 09:09:52.803: %HA_EM-6-LOG: catchall: show template interface source built-in PRINTER_INTERFACE_TEMPLATE
000098: Jan 19 09:09:52.884: %HA_EM-6-LOG: catchall: show template interface binding PRINTER_INTERFACE_TEMPLATE
000099: Jan 19 09:09:52.985: %HA_EM-6-LOG: catchall: show template interface source built-in ROUTER_INTERFACE_TEMPLATE
000100: Jan 19 09:09:53.051: %HA_EM-6-LOG: catchall: show template interface binding ROUTER_INTERFACE_TEMPLATE
000101: Jan 19 09:09:53.149: %HA_EM-6-LOG: catchall: show template interface source built-in SWITCH_INTERFACE_TEMPLATE
000102: Jan 19 09:09:53.230: %HA_EM-6-LOG: catchall: show template interface binding SWITCH_INTERFACE_TEMPLATE
000103: Jan 19 09:09:53.317: %HA_EM-6-LOG: catchall: show template interface source built-in TP_INTERFACE_TEMPLATE
000104: Jan 19 09:09:53.390: %HA_EM-6-LOG: catchall: show template interface binding TP_INTERFACE_TEMPLATE
000105: Jan 19 09:09:54.390: %HA_EM-6-LOG: catchall: show version
000106: Jan 19 09:09:54.796: %HA_EM-6-LOG: catchall: show ip interface
000107: Jan 19 09:09:54.879: %HA_EM-6-LOG: catchall: show etherchannel summary
000108: Jan 19 09:09:55.145: %HA_EM-6-LOG: catchall: show access-lists
000109: Jan 19 09:09:55.795: %HA_EM-6-LOG: catchall: show version
000110: Jan 19 09:09:55.904: %HA_EM-6-LOG: catchall: show spanning-tree
000111: Jan 19 09:09:55.970: %HA_EM-6-LOG: catchall: show spanning-tree summary
000112: Jan 19 09:09:56.085: %HA_EM-6-LOG: catchall: show vtp status
000113: Jan 19 09:09:56.204: %HA_EM-6-LOG: catchall: show vlan
000114: Jan 19 09:09:56.312: %HA_EM-6-LOG: catchall: show vlan mtu
000115: Jan 19 09:09:56.907: %HA_EM-6-LOG: catchall: show etherchannel detail
000116: Jan 19 09:09:56.973: %HA_EM-6-LOG: catchall: show file systems
000117: Jan 19 09:09:57.109: %HA_EM-6-LOG: catchall: dir flash:
000118: Jan 19 09:09:57.190: %HA_EM-6-LOG: catchall: show subsys
000119: Jan 19 09:10:15.764: %HA_EM-6-LOG: catchall: enable
000120: Jan 19 09:10:15.767: %HA_EM-6-LOG: catchall: enable
000121: Jan 19 09:10:15.819: %HA_EM-6-LOG: catchall: terminal length 0
000122: Jan 19 09:10:15.833: %HA_EM-6-LOG: catchall: terminal length 0
000123: Jan 19 09:10:15.882: %HA_EM-6-LOG: catchall: terminal width 0
000124: Jan 19 09:10:15.886: %HA_EM-6-LOG: catchall: terminal width 0
000125: Jan 19 09:10:15.966: %HA_EM-6-LOG: catchall: terminal width 0
000126: Jan 19 09:10:15.980: %HA_EM-6-LOG: catchall: show running-config
000127: Jan 19 09:10:16.333: %HA_EM-6-LOG: catchall: configure terminal
000128: Jan 19 09:10:16.816: %HA_EM-6-LOG: catchall: ip device tracking
000129: Jan 19 09:10:16.892: %HA_EM-6-LOG: catchall: ip device tracking probe delay 60
000130: Jan 19 09:10:16.966: %HA_EM-6-LOG: catchall: ip device tracking probe use-svi
000131: Jan 19 09:10:17.043: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/29
000132: Jan 19 09:10:17.085: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000133: Jan 19 09:10:17.158: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/40
000134: Jan 19 09:10:17.218: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000135: Jan 19 09:10:17.259: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/49
000136: Jan 19 09:10:17.329: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000137: Jan 19 09:10:17.438: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/46
000138: Jan 19 09:10:17.483: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000139: Jan 19 09:10:17.525: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/52
000140: Jan 19 09:10:17.567: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000141: Jan 19 09:10:17.609: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/33
000142: Jan 19 09:10:17.647: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000143: Jan 19 09:10:17.689: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/31
000144: Jan 19 09:10:17.731: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000145: Jan 19 09:10:17.773: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/36
000146: Jan 19 09:10:17.815: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000147: Jan 19 09:10:17.857: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/1
000148: Jan 19 09:10:17.899: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000149: Jan 19 09:10:17.941: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/23
000150: Jan 19 09:10:17.980: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000151: Jan 19 09:10:18.032: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/7
000152: Jan 19 09:10:18.070: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000153: Jan 19 09:10:18.112: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/27
000154: Jan 19 09:10:18.154: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000155: Jan 19 09:10:18.196: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/28
000156: Jan 19 09:10:18.238: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000157: Jan 19 09:10:18.284: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/50
000158: Jan 19 09:10:18.364: %HA_EM-6-LOG: catchall: show startup-config
000159: Jan 19 09:10:18.381: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000160: Jan 19 09:10:18.434: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/32
000161: Jan 19 09:10:18.476: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000162: Jan 19 09:10:18.518: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/12
000163: Jan 19 09:10:18.560: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000164: Jan 19 09:10:18.602: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/13
000165: Jan 19 09:10:18.644: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000166: Jan 19 09:10:18.686: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/9
000167: Jan 19 09:10:18.724: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000168: Jan 19 09:10:18.766: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/3
000169: Jan 19 09:10:18.808: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000170: Jan 19 09:10:18.850: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/15
000171: Jan 19 09:10:18.892: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000172: Jan 19 09:10:18.934: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/10
000173: Jan 19 09:10:18.972: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000174: Jan 19 09:10:19.014: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/34
000175: Jan 19 09:10:19.056: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000176: Jan 19 09:10:19.098: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/5
000177: Jan 19 09:10:19.136: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000178: Jan 19 09:10:19.182: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/39
000179: Jan 19 09:10:19.231: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000180: Jan 19 09:10:19.262: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/42
000181: Jan 19 09:10:19.311: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000182: Jan 19 09:10:19.353: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/20
000183: Jan 19 09:10:19.392: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000184: Jan 19 09:10:19.437: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/25
000185: Jan 19 09:10:19.475: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000186: Jan 19 09:10:19.521: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/35
000187: Jan 19 09:10:19.559: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000188: Jan 19 09:10:19.605: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/41
000189: Jan 19 09:10:19.643: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000190: Jan 19 09:10:19.685: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/24
000191: Jan 19 09:10:19.727: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000192: Jan 19 09:10:19.769: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/18
000193: Jan 19 09:10:19.811: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000194: Jan 19 09:10:19.853: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/38
000195: Jan 19 09:10:19.895: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000196: Jan 19 09:10:19.933: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/47
000197: Jan 19 09:10:19.975: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000198: Jan 19 09:10:20.017: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/14
000199: Jan 19 09:10:20.059: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000200: Jan 19 09:10:20.101: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/37
000201: Jan 19 09:10:20.140: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000202: Jan 19 09:10:20.196: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/51
000203: Jan 19 09:10:20.234: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000204: Jan 19 09:10:20.276: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/6
000205: Jan 19 09:10:20.335: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000206: Jan 19 09:10:20.363: %HA_EM-6-LOG: catchall: copy flash:vlan.dat scp:
000207: Jan 19 09:10:20.412: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/8
000208: Jan 19 09:10:20.486: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000209: Jan 19 09:10:20.563: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/22
000210: Jan 19 09:10:20.636: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000211: Jan 19 09:10:20.678: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/26
000212: Jan 19 09:10:20.716: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000213: Jan 19 09:10:20.758: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/2
000214: Jan 19 09:10:20.797: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000215: Jan 19 09:10:20.839: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/17
000216: Jan 19 09:10:20.881: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000217: Jan 19 09:10:20.916: %HA_EM-6-LOG: catchall: interface FastEthernet0
000218: Jan 19 09:10:20.957: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000219: Jan 19 09:10:20.999: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/44
000220: Jan 19 09:10:21.038: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000221: Jan 19 09:10:21.080: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/19
000222: Jan 19 09:10:21.118: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000223: Jan 19 09:10:21.164: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/43
000224: Jan 19 09:10:21.202: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000225: Jan 19 09:10:21.241: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/4
000226: Jan 19 09:10:21.283: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000227: Jan 19 09:10:21.321: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/45
000228: Jan 19 09:10:21.363: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000229: Jan 19 09:10:21.405: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/21
000230: Jan 19 09:10:21.447: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000231: Jan 19 09:10:21.489: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/11
000232: Jan 19 09:10:21.527: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000233: Jan 19 09:10:21.569: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/16
000234: Jan 19 09:10:21.611: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000235: Jan 19 09:10:21.653: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/30
000236: Jan 19 09:10:21.691: %HA_EM-6-LOG: catchall: ip device tracking maximum 10
000237: Jan 19 09:10:21.716: %HA_EM-6-LOG: catchall: exit
000238: Jan 19 09:10:21.723: %SYS-5-CONFIG_I: Configured from console by dnac on vty2 (10.0.0.101)
000239: Jan 19 09:10:21.761: %HA_EM-6-LOG: catchall: exit
000240: Jan 19 09:10:21.919: %HA_EM-6-LOG: catchall: exit
000241: Jan 19 09:10:23.324: %HA_EM-6-LOG: catchall: enable
000242: Jan 19 09:10:23.355: %HA_EM-6-LOG: catchall: terminal length 0
000243: Jan 19 09:10:23.387: %HA_EM-6-LOG: catchall: terminal width 0
000244: Jan 19 09:10:23.429: %HA_EM-6-LOG: catchall: write memory
000245: Jan 19 09:10:25.770: %HA_EM-6-LOG: catchall: terminal width 0
000246: Jan 19 09:10:25.788: %HA_EM-6-LOG: catchall: configure terminal
000247: Jan 19 09:10:25.837: %HA_EM-6-LOG: catchall: no crypto pki trustpoint DNAC-CA
000248: Jan 19 09:10:25.889: %HA_EM-6-LOG: catchall: crypto key zeroize rsa *
000249: Jan 19 09:10:25.900: %SYS-5-CONFIG_I: Configured from console by dnac on vty2 (10.0.0.101)
000250: Jan 19 09:10:25.973: %HA_EM-6-LOG: catchall: exit
000251: Jan 19 09:10:26.469: %HA_EM-6-LOG: catchall: write memory
000252: Jan 19 09:10:28.357: %HA_EM-6-LOG: catchall: terminal width 0
000253: Jan 19 09:10:28.374: %HA_EM-6-LOG: catchall: configure terminal
000254: Jan 19 09:10:28.423: %HA_EM-6-LOG: catchall: ip http client source-interface Vlan1
000255: Jan 19 09:10:28.476: %HA_EM-6-LOG: catchall: ip ssh source-interface Vlan1
000256: Jan 19 09:10:28.500: %HA_EM-6-LOG: catchall: ip ssh version 2
000257: Jan 19 09:10:28.532: %HA_EM-6-LOG: catchall: ip domain lookup
000258: Jan 19 09:10:28.577: %HA_EM-6-LOG: catchall: crypto pki trustpoint DNAC-CA
000259: Jan 19 09:10:28.612: %HA_EM-6-LOG: catchall: enrollment mode ra
000260: Jan 19 09:10:28.644: %HA_EM-6-LOG: catchall: enrollment terminal
000261: Jan 19 09:10:28.678: %HA_EM-6-LOG: catchall: usage ssl-client
000262: Jan 19 09:10:28.717: %HA_EM-6-LOG: catchall: revocation-check crl none
000263: Jan 19 09:10:28.731: %HA_EM-6-LOG: catchall: exit
000264: Jan 19 09:10:28.776: %HA_EM-6-LOG: catchall: crypto pki authenticate DNAC-CA
000265: Jan 19 09:10:30.520: %SYS-5-CONFIG_I: Configured from console by dnac on vty2 (10.0.0.101)
000266: Jan 19 09:10:30.597: %HA_EM-6-LOG: catchall: exit
000267: Jan 19 09:10:31.314: %HA_EM-6-LOG: catchall: terminal width 0
000268: Jan 19 09:10:31.342: %HA_EM-6-LOG: catchall: configure terminal
000269: Jan 19 09:10:31.527: %HA_EM-6-LOG: catchall: snmp-server host 10.0.0.201 traps version 2c * udp-port 162
000270: Jan 19 09:10:31.555: %HA_EM-6-LOG: catchall: snmp-server enable traps
000271: Jan 19 09:10:31.573: %SYS-5-CONFIG_I: Configured from console by dnac on vty2 (10.0.0.101)
000272: Jan 19 09:10:31.601: %HA_EM-6-LOG: catchall: exit
000273: Jan 19 09:10:32.181: %HA_EM-6-LOG: catchall: write memory
000276: Jan 19 09:10:34.767: %SYS-6-LOGGINGHOST_STARTSTOP: Logging to host 10.0.0.201 port 0 CLI Request Triggered
000277: Jan 19 09:10:34.774: %HA_EM-6-LOG: catchall: logging host 10.0.0.201 transport udp port 514
000278: Jan 19 09:10:34.788: %SYS-6-LOGGINGHOST_STARTSTOP: Logging to host 10.0.0.201 port 514 started - CLI initiated
000279: Jan 19 09:10:34.809: %HA_EM-6-LOG: catchall: logging trap 6
000280: Jan 19 09:10:34.830: %SYS-5-CONFIG_I: Configured from console by dnac on vty2 (10.0.0.101)
000281: Jan 19 09:10:34.858: %HA_EM-6-LOG: catchall: exit
000282: Jan 19 09:10:35.431: %HA_EM-6-LOG: catchall: write memory
2960X_PnP-TEST>
Phew! +280 entries!! Let’s break it down a bit…
First off we see some messages in the beginning that you normally do not see. Like the Op-43 Msg:. This is due to the 5A1D in the Option 43 string of the DHCP pool. “D” for Debug. In normal circumstances this option code should be 5A1N. “N” for normal.
The very first configuration changes are these:
Jan 19 09:05:09.289: %SYS-6-CLOCKUPDATE: System clock has been updated from 09:05:04 UTC Sun Jan 19 2020 to 09:05:09 UTC Sun Jan 19 2020, configured from console by console.
Jan 19 09:05:09.537: %PKI-4-NOCONFIGAUTOSAVE: Configuration was modified. Issue "write memory" to save new IOS PKI configuration
000041: Jan 19 09:09:13.045: %SSH-5-ENABLED: SSH 1.99 has been enabled
000042: Jan 19 09:09:13.331: Configuring snmpv3 USM user, persisting snmpEngineBoots. Please Wait...
000043: Jan 19 09:09:13.541: %PARSER-4-BADCFG: Unexpected end of configuration file.
This is PnP configuring basic connectivity to the switch like adding credentials (CLI and SNMP) and configuring SSH. These credentials are required for DNAC to be able to add the device to its inventory. The reason we see the new PKI configuration is that DNAC which is our PnP server installs a certificate used for PnP communication. And obviously the clock has to be in sync, hence this is set before the cert is installed. The certificate installation happens before executing the PnP workflow!
The last line 000043: Jan 19 09:09:13.541: %PARSER-4-BADCFG: Unexpected end of configuration file. is normal. I’ve seen this before as a final message telling that PnP onboarding is done. I believe it’s a cosmetic bug.
Now that DNAC has finished with PnP onboarding, it starts collecting information about the switch using various show commands. It also saves the configuration 000046: Jan 19 09:09:34.401: %HA_EM-6-LOG: catchall: copy running-config startup-config
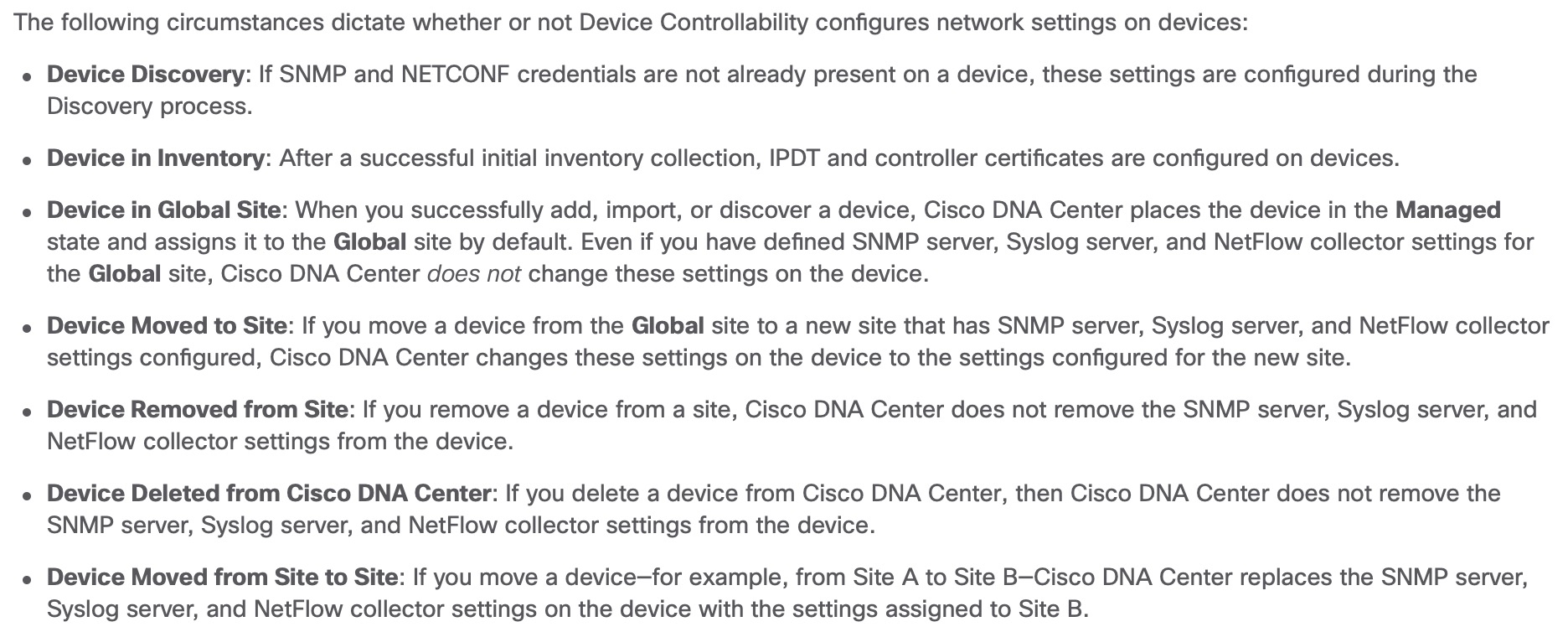
after which it starts configuring IP Device Tracking (IPDT). This is part of the Device Controllability feature which is enabled by default. You can find a description in the settings:
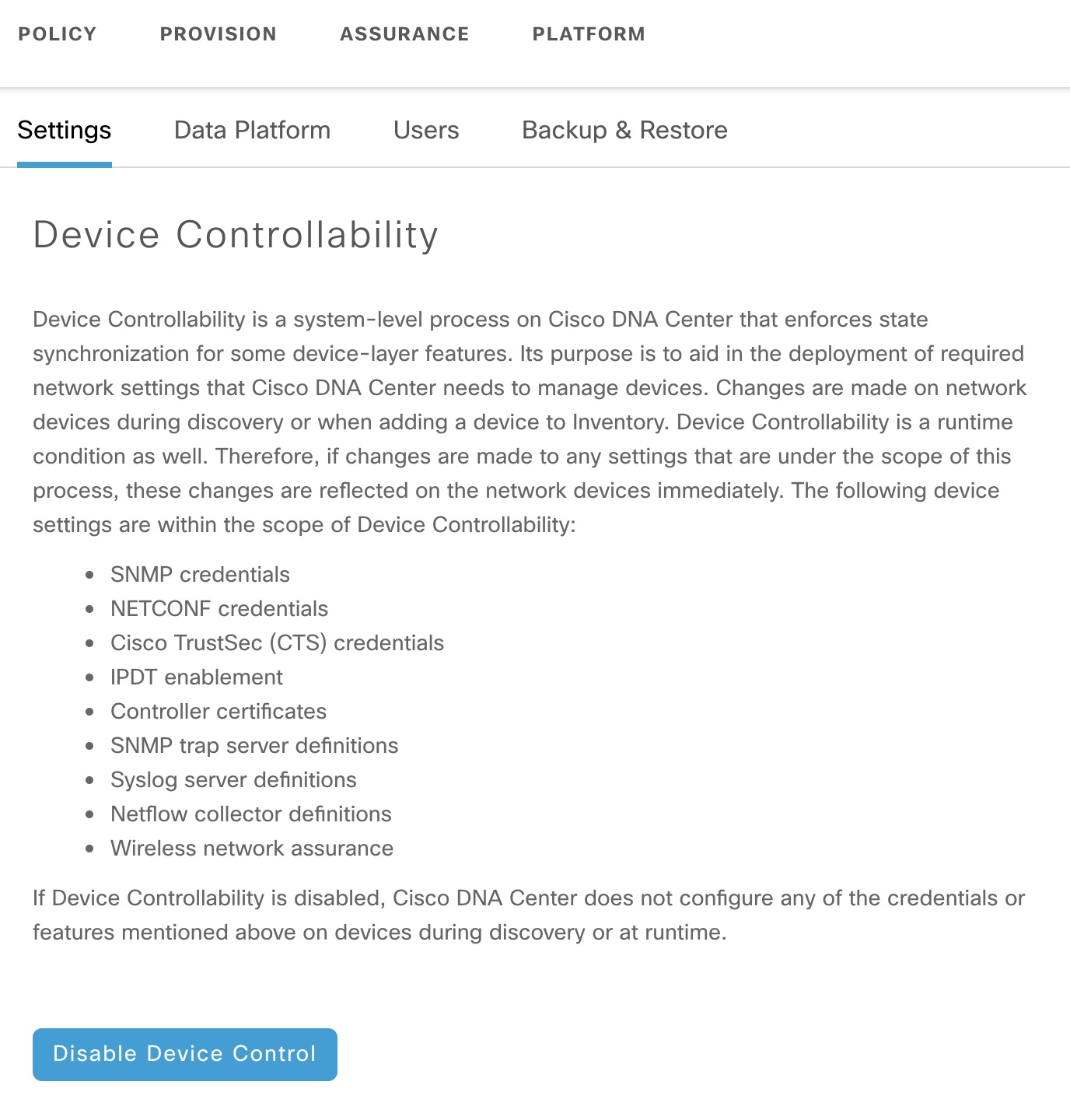
Device controllability configuration is done only upon onboarding using PnP or adding devices to the inventory using a Discovery job. Although they say that changes are made when adding a device to inventory I have not seen it happen when you manually add the 2960X directly to a site in this setup. In fact, this is what the current documentation says:
After configuring IPDT it saves the configurating using write memory this time.
000239: Jan 19 09:10:21.761: %HA_EM-6-LOG: catchall: exit
000240: Jan 19 09:10:21.919: %HA_EM-6-LOG: catchall: exit
000241: Jan 19 09:10:23.324: %HA_EM-6-LOG: catchall: enable
000242: Jan 19 09:10:23.355: %HA_EM-6-LOG: catchall: terminal length 0
000243: Jan 19 09:10:23.387: %HA_EM-6-LOG: catchall: terminal width 0
000244: Jan 19 09:10:23.429: %HA_EM-6-LOG: catchall: write memory
000245: Jan 19 09:10:25.770: %HA_EM-6-LOG: catchall: terminal width 0
000246: Jan 19 09:10:25.788: %HA_EM-6-LOG: catchall: configure terminal
000247: Jan 19 09:10:25.837: %HA_EM-6-LOG: catchall: no crypto pki trustpoint DNAC-CA
000248: Jan 19 09:10:25.889: %HA_EM-6-LOG: catchall: crypto key zeroize rsa *
000249: Jan 19 09:10:25.900: %SYS-5-CONFIG_I: Configured from console by dnac on vty2 (10.0.0.101)
000250: Jan 19 09:10:25.973: %HA_EM-6-LOG: catchall: exit
000251: Jan 19 09:10:26.469: %HA_EM-6-LOG: catchall: write memory
PnP tries to delete the DNAC certificate. This is odd as we’re in the process of doing device onboarding using ZTP with PnP meaning configuring a new device out of box. Clearly DNAC doesn’t take this fact into account when addind a device to its inventory. Had we been adding a device using a Discovery job, I could understand it as brownfield configuration could exist. Again, the configuration is saved.
Next, it looks like DNAC tries to clear all rsa keys using the crypto key zeroize rsa * command, yet SSH still works. Let’s see what happens when we try to execute this command on the switch:
2960X_PnP-TEST#conf t
Enter configuration commands, one per line. End with CNTL/Z.
2960X_PnP-TEST(config)#
000377: Jan 19 09:28:19.879: %HA_EM-6-LOG: catchall: configure terminal
2960X_PnP-TEST(config)#crypto key zeroize rsa *
% The specified keypair does not exist (*).
2960X_PnP-TEST(config)#
000378: Jan 19 09:28:25.126: %HA_EM-6-LOG: catchall: crypto key zeroize rsa *
2960X_PnP-TEST(config)#crypto key zeroize rsa ?
WORD keypair label
<cr>
2960X_PnP-TEST(config)#crypto key zeroize rsa
That’s funny! I wonder when we could see a key pair with label the * in a configuration. Sure it is possible to configure such a key pair. I’ve just never seen it before.
000252: Jan 19 09:10:28.357: %HA_EM-6-LOG: catchall: terminal width 0
000253: Jan 19 09:10:28.374: %HA_EM-6-LOG: catchall: configure terminal
000254: Jan 19 09:10:28.423: %HA_EM-6-LOG: catchall: ip http client source-interface Vlan1
000255: Jan 19 09:10:28.476: %HA_EM-6-LOG: catchall: ip ssh source-interface Vlan1
000256: Jan 19 09:10:28.500: %HA_EM-6-LOG: catchall: ip ssh version 2
000257: Jan 19 09:10:28.532: %HA_EM-6-LOG: catchall: ip domain lookup
000258: Jan 19 09:10:28.577: %HA_EM-6-LOG: catchall: crypto pki trustpoint DNAC-CA
000259: Jan 19 09:10:28.612: %HA_EM-6-LOG: catchall: enrollment mode ra
000260: Jan 19 09:10:28.644: %HA_EM-6-LOG: catchall: enrollment terminal
000261: Jan 19 09:10:28.678: %HA_EM-6-LOG: catchall: usage ssl-client
000262: Jan 19 09:10:28.717: %HA_EM-6-LOG: catchall: revocation-check crl none
000263: Jan 19 09:10:28.731: %HA_EM-6-LOG: catchall: exit
000264: Jan 19 09:10:28.776: %HA_EM-6-LOG: catchall: crypto pki authenticate DNAC-CA
Above both HTTP and SSH client source interface are configured. The first tells DNAC which IP address to use to manage the device. The latter I don’t know exactly why DNAC configures. Perhaps it could be useful for devices with multiple interfaces to ensure that if you SSH from that router, you use the management interface as source. Especially in environments with VRFs configured.
Domain lookups are enabled and now the DNAC certificate is installed. It makes the device trust DNAC when communicating using HTTPS. One application that might do this is SWIM (Software Image Management).
Finally the SNMP trap server and syslog are configured:
000267: Jan 19 09:10:31.314: %HA_EM-6-LOG: catchall: terminal width 0
000268: Jan 19 09:10:31.342: %HA_EM-6-LOG: catchall: configure terminal
000269: Jan 19 09:10:31.527: %HA_EM-6-LOG: catchall: snmp-server host 10.0.0.201 traps version 2c * udp-port 162
000270: Jan 19 09:10:31.555: %HA_EM-6-LOG: catchall: snmp-server enable traps
000271: Jan 19 09:10:31.573: %SYS-5-CONFIG_I: Configured from console by dnac on vty2 (10.0.0.101)
000272: Jan 19 09:10:31.601: %HA_EM-6-LOG: catchall: exit
000273: Jan 19 09:10:32.181: %HA_EM-6-LOG: catchall: write memory
000276: Jan 19 09:10:34.767: %SYS-6-LOGGINGHOST_STARTSTOP: Logging to host 10.0.0.201 port 0 CLI Request Triggered
000277: Jan 19 09:10:34.774: %HA_EM-6-LOG: catchall: logging host 10.0.0.201 transport udp port 514
000278: Jan 19 09:10:34.788: %SYS-6-LOGGINGHOST_STARTSTOP: Logging to host 10.0.0.201 port 514 started - CLI initiated
000279: Jan 19 09:10:34.809: %HA_EM-6-LOG: catchall: logging trap 6
000280: Jan 19 09:10:34.830: %SYS-5-CONFIG_I: Configured from console by dnac on vty2 (10.0.0.101)
000281: Jan 19 09:10:34.858: %HA_EM-6-LOG: catchall: exit
000282: Jan 19 09:10:35.431: %HA_EM-6-LOG: catchall: write memory
Both server configurations point to DNAC’s VIP of the Enterprise interface, 10.0.0.201 in this example.
Notice the SNMP trap configuration. It uses a version 2c community (only an asterisk is shown above). The community string configured when using SNMPv3 is the username of your SNMPv3 configuration. The reason why DNAC is configuring SNMP v2c traps is that currently DNAC doesn’t support SNMPv3 for its assurance feature. Take a look at the WARNING message here:
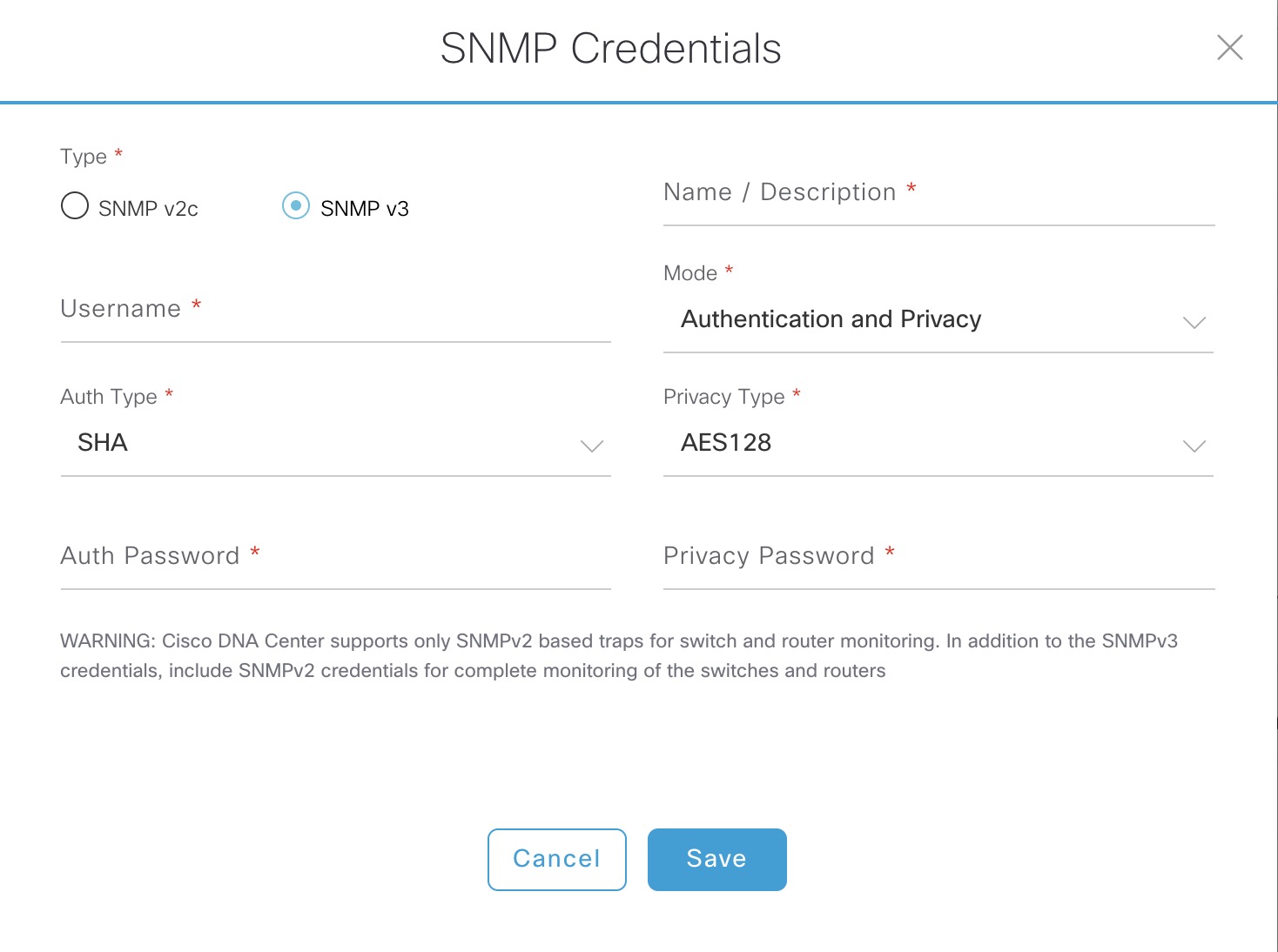
Keep this in mind if you have strict security policies. Remember these settings (Syslog and SNMP servers) come from the Design - Network Settings - Network page of DNAC and they are enabled by default.
Conclusion
A lot of things happen in the background when onboarding devices using DNAC. In summary this was provisioned:
- Device credentials (CLI and SNMP)
- IPDT
- Syslog to DNAC at information level
- HTTP client source interface
- SSH source interface
- SSH version 2
- Domain lookups
- DNAC certificate
- SNMP traps to DNAC (using v2c)
We also noticed a lot of write memory throughout the configuration.
I hope this was an interesting read for you. I always like to open the hood and see what’s going on beheath it.
