DNA Center - Provision - What It Does To Your Devices
Table of Contents
In this post I’m using DNAC version 1.3.3.3 to demonstrate what DNAC does to your device when configuring the network settings in DNAC.
Previously I’ve written similar posts:
DNA Center - PnP - What It Does To Your Devices DNA Center - Discovery - What It Does To Your Devices
Test Case
One simple test case is all we need to see what DNAC does:
- Manually configure a Catalyst 9300 switch
- Add the switch to DNAC manually via inventory
Topology
The below topology is used for this post:
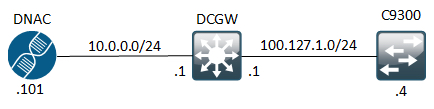
DCGW is the L3 switch routing between the two connected networks. Since we’re looking at DNAC provisioning we need to ensure that DNAC can in fact add the switch to its inventory. The prerequisites of DNAC being able to manage devices are:
DNAC must have:
- SSH access
- Privilege level 15
- SNMP access
- SNMPv2c read at a minimum
The initial configuration for adding the device is this:
hostname C9300
!
int vlan1
ip address dhcp
!
snmp-server community dnac ro
username dnac privilege 15 algorithm-type sha256 secret <mysecret>
!
crypto key gen rsa mod 2048 label SSH
!
line vty 0 15
login local
!
event manager applet catchall
event cli pattern ".*" sync no skip no
action 1 syslog msg "$_cli_msg"
In DNAC Provision you can manually add devices to the inventory:
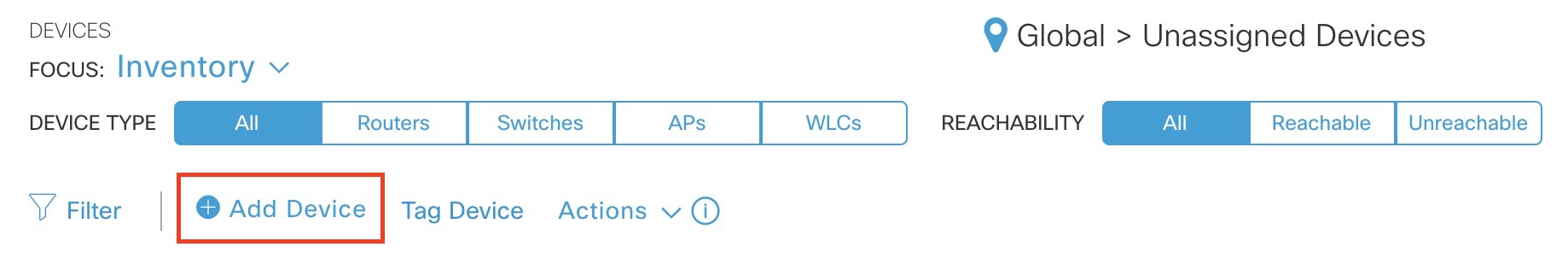
In the add device windows we see the mandatory fields:
- Type
- Device IP / DNA Name
- SNMP
- CLI
NOTE! For CLI credentials the enable password is optional.
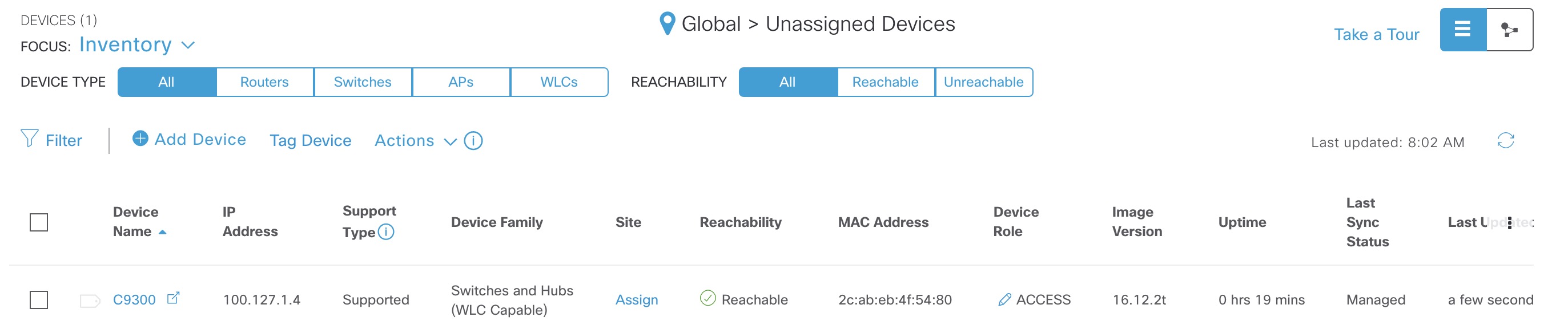
The device will be added to the Unassigned Devices section:
Right after adding the device DNAC will go out and sync the device’s configuration and do some other things. Here is the complete list of commands seen on the device:
C9300#
*Mar 27 07:00:02.955: %HA_EM-6-LOG: catchall: write
*Mar 27 07:00:26.019: %SEC_LOGIN-5-LOGIN_SUCCESS: Login Success [user: dnac] [Source: 10.0.0.101] [localport: 22] at 07:00:26 UTC Fri Mar 27 2020
*Mar 27 07:00:26.030: %HA_EM-6-LOG: catchall: enable
*Mar 27 07:00:26.160: %SEC_LOGIN-5-LOGIN_SUCCESS: Login Success [user: dnac] [Source: 10.0.0.101] [localport: 22] at 07:00:26 UTC Fri Mar 27 2020
*Mar 27 07:00:26.171: %HA_EM-6-LOG: catchall: enable
*Mar 27 07:00:26.179: %HA_EM-6-LOG: catchall: terminal length 0
*Mar 27 07:00:26.199: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 07:00:26.261: %HA_EM-6-LOG: catchall: show platform software process list switch active R0 name wncd_0
*Mar 27 07:00:27.470: %SEC_LOGIN-5-LOGIN_SUCCESS: Login Success [user: dnac] [Source: 10.0.0.101] [localport: 22] at 07:00:27 UTC Fri Mar 27 2020
*Mar 27 07:00:27.484: %HA_EM-6-LOG: catchall: enable
*Mar 27 07:00:27.499: %HA_EM-6-LOG: catchall: terminal length 0
*Mar 27 07:00:27.519: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 07:00:27.544: %HA_EM-6-LOG: catchall: show running-config
*Mar 27 07:00:27.830: %HA_EM-6-LOG: catchall: show auto qos
*Mar 27 07:00:27.887: %HA_EM-6-LOG: catchall: show ip nbar protocol-pack loaded
*Mar 27 07:00:27.921: %HA_EM-6-LOG: catchall: show ip nbar version
*Mar 27 07:00:27.948: %HA_EM-6-LOG: catchall: show file systems
*Mar 27 07:00:28.001: %HA_EM-6-LOG: catchall: show ip nbar protocol-id
*Mar 27 07:00:28.146: %HA_EM-6-LOG: catchall: show ip nbar attribute sub-category
*Mar 27 07:00:28.180: %HA_EM-6-LOG: catchall: show ip nbar attribute category
*Mar 27 07:00:28.211: %HA_EM-6-LOG: catchall: show ip nbar attribute
*Mar 27 07:00:28.526: %HA_EM-6-LOG: catchall: show ip access-lists
*Mar 27 07:00:28.568: %HA_EM-6-LOG: catchall: show running-config
*Mar 27 07:00:28.762: %HA_EM-6-LOG: catchall: show ipv6 access-list
*Mar 27 07:00:28.794: %HA_EM-6-LOG: catchall: show hosts
*Mar 27 07:00:28.847: %HA_EM-6-LOG: catchall: show running-config
*Mar 27 07:00:29.148: %HA_EM-6-LOG: catchall: show ip igmp snooping
*Mar 27 07:00:29.193: %HA_EM-6-LOG: catchall: show vrf detail
*Mar 27 07:00:29.229: %HA_EM-6-LOG: catchall: show ip route summary
*Mar 27 07:00:29.257: %HA_EM-6-LOG: catchall: show ip route
*Mar 27 07:00:29.292: %HA_EM-6-LOG: catchall: show flow monitor
*Mar 27 07:00:29.331: %HA_EM-6-LOG: catchall: show interfaces
*Mar 27 07:00:29.485: %HA_EM-6-LOG: catchall: show version
*Mar 27 07:00:29.570: %HA_EM-6-LOG: catchall: show ip ospf
*Mar 27 07:00:29.593: %HA_EM-6-LOG: catchall: show ospfv3
*Mar 27 07:00:29.620: %HA_EM-6-LOG: catchall: show ip ospf interface
*Mar 27 07:00:29.650: %HA_EM-6-LOG: catchall: show redundancy
*Mar 27 07:00:29.678: %HA_EM-6-LOG: catchall: show standby
*Mar 27 07:00:29.704: %HA_EM-6-LOG: catchall: show cef state
*Mar 27 07:00:29.744: %HA_EM-6-LOG: catchall: show flow monitor
*Mar 27 07:00:29.775: %HA_EM-6-LOG: catchall: show logging
*Mar 27 07:00:29.802: %HA_EM-6-LOG: catchall: show snmp
*Mar 27 07:00:29.827: %HA_EM-6-LOG: catchall: show snmp host
*Mar 27 07:00:29.868: %HA_EM-6-LOG: catchall: show cef interface brief
*Mar 27 07:00:29.900: %HA_EM-6-LOG: catchall: show ip vrf brief
*Mar 27 07:00:29.945: %HA_EM-6-LOG: catchall: show ip route vrf Mgmt-vrf summary
*Mar 27 07:00:29.997: %HA_EM-6-LOG: catchall: show clock
*Mar 27 07:00:30.046: %HA_EM-6-LOG: catchall: disable
*Mar 27 07:00:30.047: %SYS-6-LOGOUT: User dnac has exited tty session 3(10.0.0.101)
*Mar 27 07:00:30.048: %HA_EM-6-LOG: catchall: logout
*Mar 27 07:00:30.254: %SEC_LOGIN-5-LOGIN_SUCCESS: Login Success [user: dnac] [Source: 10.0.0.101] [localport: 22] at 07:00:30 UTC Fri Mar 27 2020
*Mar 27 07:00:30.268: %HA_EM-6-LOG: catchall: enable
*Mar 27 07:00:30.274: %HA_EM-6-LOG: catchall: terminal length 0
*Mar 27 07:00:30.293: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 07:00:30.309: %HA_EM-6-LOG: catchall: show version
*Mar 27 07:00:30.414: %HA_EM-6-LOG: catchall: show device-tracking database address all
*Mar 27 07:00:30.443: %HA_EM-6-LOG: catchall: show arp
*Mar 27 07:00:30.474: %HA_EM-6-LOG: catchall: show mac address-table
*Mar 27 07:00:30.548: %HA_EM-6-LOG: catchall: show interfaces switchport
*Mar 27 07:00:30.803: %HA_EM-6-LOG: catchall: show lldp neighbors detail
*Mar 27 07:00:30.899: %HA_EM-6-LOG: catchall: show cdp neighbors detail
*Mar 27 07:00:30.950: %HA_EM-6-LOG: catchall: show processes platform
*Mar 27 07:00:40.374: %HA_EM-6-LOG: catchall: show monitor session all
*Mar 27 07:00:40.680: %HA_EM-6-LOG: catchall: show ip nbar protocol-pack active
*Mar 27 07:00:40.718: %HA_EM-6-LOG: catchall: show romvar
*Mar 27 07:00:40.765: %HA_EM-6-LOG: catchall: show redundancy states
*Mar 27 07:00:40.820: %HA_EM-6-LOG: catchall: show crypto pki certificates
*Mar 27 07:00:40.893: %HA_EM-6-LOG: catchall: show ip nbar control-plane
*Mar 27 07:00:40.921: %HA_EM-6-LOG: catchall: show flow interface
*Mar 27 07:00:40.966: %HA_EM-6-LOG: catchall: show processes cpu
*Mar 27 07:00:40.991: %HA_EM-6-LOG: catchall: show license usage
*Mar 27 07:00:41.041: %HA_EM-6-LOG: catchall: show platform software et-analytics global
*Mar 27 07:00:41.086: %HA_EM-6-LOG: catchall: show flow record
*Mar 27 07:00:41.114: %HA_EM-6-LOG: catchall: show flow exporter
*Mar 27 07:00:41.205: %HA_EM-6-LOG: catchall: show running-config all
*Mar 27 07:00:41.607: %HA_EM-6-LOG: catchall: show license all
*Mar 27 07:00:41.651: %HA_EM-6-LOG: catchall: show license tech support
*Mar 27 07:00:41.687: %HA_EM-6-LOG: catchall: show license summary
*Mar 27 07:00:41.718: %HA_EM-6-LOG: catchall: show ap summary
*Mar 27 07:00:41.759: %HA_EM-6-LOG: catchall: show wireless summary
*Mar 27 07:00:41.770: %HA_EM-6-LOG: catchall: disable
*Mar 27 07:00:41.781: %SYS-6-LOGOUT: User dnac has exited tty session 3(10.0.0.101)
*Mar 27 07:00:42.106: %SEC_LOGIN-5-LOGIN_SUCCESS: Login Success [user: dnac] [Source: 10.0.0.101] [localport: 22] at 07:00:42 UTC Fri Mar 27 2020
*Mar 27 07:00:42.119: %HA_EM-6-LOG: catchall: enable
*Mar 27 07:00:42.127: %HA_EM-6-LOG: catchall: terminal length 0
*Mar 27 07:00:42.150: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 07:00:42.166: %HA_EM-6-LOG: catchall: show wireless summary
*Mar 27 07:00:42.174: %HA_EM-6-LOG: catchall: disable
*Mar 27 07:00:42.419: %SEC_LOGIN-5-LOGIN_SUCCESS: Login Success [user: dnac] [Source: 10.0.0.101] [localport: 22] at 07:00:42 UTC Fri Mar 27 2020
*Mar 27 07:00:42.434: %HA_EM-6-LOG: catchall: enable
*Mar 27 07:00:42.442: %HA_EM-6-LOG: catchall: terminal length 0
*Mar 27 07:00:42.462: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 07:00:42.548: %HA_EM-6-LOG: catchall: show wireless summary
*Mar 27 07:00:42.561: %HA_EM-6-LOG: catchall: disable
*Mar 27 07:00:42.895: %SEC_LOGIN-5-LOGIN_SUCCESS: Login Success [user: dnac] [Source: 10.0.0.101] [localport: 22] at 07:00:42 UTC Fri Mar 27 2020
*Mar 27 07:00:42.905: %HA_EM-6-LOG: catchall: enable
*Mar 27 07:00:42.914: %HA_EM-6-LOG: catchall: terminal length 0
*Mar 27 07:00:42.928: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 07:00:42.947: %HA_EM-6-LOG: catchall: show lacp sys-id
*Mar 27 07:00:42.981: %HA_EM-6-LOG: catchall: show etherchannel load-balance
*Mar 27 07:00:43.010: %HA_EM-6-LOG: catchall: show etherchannel detail
*Mar 27 07:00:43.035: %HA_EM-6-LOG: catchall: show running-config
*Mar 27 07:00:43.245: %HA_EM-6-LOG: catchall: terminal length 0
*Mar 27 07:00:43.308: %HA_EM-6-LOG: catchall: show interfaces
*Mar 27 07:00:43.467: %HA_EM-6-LOG: catchall: show iox-service detail
*Mar 27 07:00:43.469: %HA_EM-6-LOG: catchall: show platform software iox-service
*Mar 27 07:00:43.592: %HA_EM-6-LOG: catchall: show platform software process list switch active R0 name caf
*Mar 27 07:00:43.638: %HA_EM-6-LOG: catchall: show platform software process list switch active R0 name libvirtd
*Mar 27 07:00:43.683: %HA_EM-6-LOG: catchall: show platform software process list switch active R0 name dockerd
*Mar 27 07:00:43.762: %HA_EM-6-LOG: catchall: show ip interface brief
*Mar 27 07:00:43.827: %HA_EM-6-LOG: catchall: show version
*Mar 27 07:00:43.881: %HA_EM-6-LOG: catchall: show running-config
*Mar 27 07:00:44.079: %HA_EM-6-LOG: catchall: show ip http server session-module
*Mar 27 07:00:44.191: %HA_EM-6-LOG: catchall: show module
*Mar 27 07:00:44.507: %HA_EM-6-LOG: catchall: show ip interface
*Mar 27 07:00:44.572: %HA_EM-6-LOG: catchall: show etherchannel summary
*Mar 27 07:00:44.648: %HA_EM-6-LOG: catchall: show access-lists
*Mar 27 07:00:44.908: %HA_EM-6-LOG: catchall: show version
*Mar 27 07:00:44.964: %HA_EM-6-LOG: catchall: show spanning-tree
*Mar 27 07:00:44.999: %HA_EM-6-LOG: catchall: show spanning-tree summary
*Mar 27 07:00:45.071: %HA_EM-6-LOG: catchall: show vtp status
*Mar 27 07:00:45.168: %HA_EM-6-LOG: catchall: show vlan
*Mar 27 07:00:45.211: %HA_EM-6-LOG: catchall: show vlan mtu
*Mar 27 07:00:45.351: %HA_EM-6-LOG: catchall: show template
*Mar 27 07:00:45.423: %HA_EM-6-LOG: catchall: show template interface source built-in AP_INTERFACE_TEMPLATE
*Mar 27 07:00:45.483: %HA_EM-6-LOG: catchall: show template interface binding AP_INTERFACE_TEMPLATE
*Mar 27 07:00:45.543: %HA_EM-6-LOG: catchall: show template interface source built-in DMP_INTERFACE_TEMPLATE
*Mar 27 07:00:45.574: %HA_EM-6-LOG: catchall: show template interface binding DMP_INTERFACE_TEMPLATE
*Mar 27 07:00:45.637: %HA_EM-6-LOG: catchall: show template interface source built-in IP_CAMERA_INTERFACE_TEMPLATE
*Mar 27 07:00:45.692: %HA_EM-6-LOG: catchall: show template interface binding IP_CAMERA_INTERFACE_TEMPLATE
*Mar 27 07:00:45.754: %HA_EM-6-LOG: catchall: show template interface source built-in IP_PHONE_INTERFACE_TEMPLATE
*Mar 27 07:00:45.805: %HA_EM-6-LOG: catchall: show template interface binding IP_PHONE_INTERFACE_TEMPLATE
*Mar 27 07:00:45.863: %HA_EM-6-LOG: catchall: show template interface source built-in LAP_INTERFACE_TEMPLATE
*Mar 27 07:00:45.915: %HA_EM-6-LOG: catchall: show template interface binding LAP_INTERFACE_TEMPLATE
*Mar 27 07:00:45.979: %HA_EM-6-LOG: catchall: show template interface source built-in MSP_CAMERA_INTERFACE_TEMPLATE
*Mar 27 07:00:46.036: %HA_EM-6-LOG: catchall: show template interface binding MSP_CAMERA_INTERFACE_TEMPLATE
*Mar 27 07:00:46.076: %HA_EM-6-LOG: catchall: show template interface source built-in MSP_VC_INTERFACE_TEMPLATE
*Mar 27 07:00:46.125: %HA_EM-6-LOG: catchall: show template interface binding MSP_VC_INTERFACE_TEMPLATE
*Mar 27 07:00:46.175: %HA_EM-6-LOG: catchall: show template interface source built-in PRINTER_INTERFACE_TEMPLATE
*Mar 27 07:00:46.232: %HA_EM-6-LOG: catchall: show template interface binding PRINTER_INTERFACE_TEMPLATE
*Mar 27 07:00:46.295: %HA_EM-6-LOG: catchall: show template interface source built-in ROUTER_INTERFACE_TEMPLATE
*Mar 27 07:00:46.351: %HA_EM-6-LOG: catchall: show template interface binding ROUTER_INTERFACE_TEMPLATE
*Mar 27 07:00:46.414: %HA_EM-6-LOG: catchall: show template interface source built-in SWITCH_INTERFACE_TEMPLATE
*Mar 27 07:00:46.469: %HA_EM-6-LOG: catchall: show template interface binding SWITCH_INTERFACE_TEMPLATE
*Mar 27 07:00:46.528: %HA_EM-6-LOG: catchall: show template interface source built-in TP_INTERFACE_TEMPLATE
*Mar 27 07:00:46.574: %HA_EM-6-LOG: catchall: show template interface binding TP_INTERFACE_TEMPLATE
*Mar 27 07:00:46.631: %HA_EM-6-LOG: catchall: show install summary
*Mar 27 07:00:48.403: %HA_EM-6-LOG: catchall: show install summary
*Mar 27 07:00:50.054: %HA_EM-6-LOG: catchall: show version
*Mar 27 07:00:50.099: %HA_EM-6-LOG: catchall: show install rollback
*Mar 27 07:00:50.733: %HA_EM-6-LOG: catchall: dir flash:
*Mar 27 07:00:51.296: %HA_EM-6-LOG: catchall: show subsys
*Mar 27 07:00:51.412: %HA_EM-6-LOG: catchall: show running-config
*Mar 27 07:00:54.606: %SEC_LOGIN-5-LOGIN_SUCCESS: Login Success [user: dnac] [Source: 10.0.0.101] [localport: 22] at 07:00:54 UTC Fri Mar 27 2020
*Mar 27 07:00:54.613: %HA_EM-6-LOG: catchall: enable
*Mar 27 07:00:54.617: %HA_EM-6-LOG: catchall: terminal length 0
*Mar 27 07:00:54.622: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 07:00:54.629: %HA_EM-6-LOG: catchall: show license eventlog 0
*Mar 27 07:00:58.210: %HA_EM-6-LOG: catchall: show running-config
*Mar 27 07:00:58.995: %HA_EM-6-LOG: catchall: show startup-config
*Mar 27 07:01:00.766: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 07:01:00.779: %HA_EM-6-LOG: catchall: configure terminal
*Mar 27 07:01:00.811: %HA_EM-6-LOG: catchall: no crypto pki trustpoint DNAC-CA
*Mar 27 07:01:00.842: %HA_EM-6-LOG: catchall: crypto key zeroize rsa DNAC-CA
*Mar 27 07:01:00.864: %SYS-5-CONFIG_I: Configured from console by dnac on vty3 (10.0.0.101)
*Mar 27 07:01:00.865: %HA_EM-6-LOG: catchall: exit
*Mar 27 07:01:03.175: %HA_EM-6-LOG: catchall: write memory
*Mar 27 07:01:03.755: %HA_EM-6-LOG: catchall: copy flash:vlan.dat scp:
*Mar 27 07:01:03.842: %HA_EM-6-LOG: catchall: disable
*Mar 27 07:01:03.849: %SYS-6-LOGOUT: User dnac has exited tty session 4(10.0.0.101)
*Mar 27 07:01:04.301: %SEC_LOGIN-5-LOGIN_SUCCESS: Login Success [user: dnac] [Source: 10.0.0.101] [localport: 22] at 07:01:04 UTC Fri Mar 27 2020
*Mar 27 07:01:04.315: %HA_EM-6-LOG: catchall: enable
*Mar 27 07:01:04.325: %HA_EM-6-LOG: catchall: terminal length 0
*Mar 27 07:01:04.343: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 07:01:04.363: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 07:01:04.375: %HA_EM-6-LOG: catchall: configure terminal
*Mar 27 07:01:04.403: %SYS-5-CONFIG_I: Configured from console by dnac on vty3 (10.0.0.101)
*Mar 27 07:01:04.404: %HA_EM-6-LOG: catchall: exit
*Mar 27 07:01:04.415: %HA_EM-6-LOG: catchall: disable
*Mar 27 07:01:05.331: %SEC_LOGIN-5-LOGIN_SUCCESS: Login Success [user: dnac] [Source: 10.0.0.101] [localport: 22] at 07:01:05 UTC Fri Mar 27 2020
*Mar 27 07:01:05.351: %HA_EM-6-LOG: catchall: enable
*Mar 27 07:01:05.361: %HA_EM-6-LOG: catchall: terminal length 0
*Mar 27 07:01:05.377: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 07:01:05.393: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 07:01:05.402: %HA_EM-6-LOG: catchall: configure terminal
*Mar 27 07:01:05.429: %HA_EM-6-LOG: catchall: device-tracking tracking
*Mar 27 07:01:05.461: %HA_EM-6-LOG: catchall: device-tracking policy IPDT_MAX_10
*Mar 27 07:01:05.483: %HA_EM-6-LOG: catchall: limit address-count 10
*Mar 27 07:01:05.500: %HA_EM-6-LOG: catchall: tracking enable
*Mar 27 07:01:05.538: %HA_EM-6-LOG: catchall: interface AppGigabitEthernet1/0/1
*Mar 27 07:01:05.571: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:05.578: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/42
*Mar 27 07:01:05.606: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:05.633: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/32
*Mar 27 07:01:05.665: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:05.693: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/41
*Mar 27 07:01:05.722: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:05.748: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/8
*Mar 27 07:01:05.775: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:05.791: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/43
*Mar 27 07:01:05.805: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:05.833: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/14
*Mar 27 07:01:05.871: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:05.896: %HA_EM-6-LOG: catchall: interface Bluetooth0/4
*Mar 27 07:01:05.955: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/39
*Mar 27 07:01:05.987: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:06.013: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/29
*Mar 27 07:01:06.043: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:06.070: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/1/3
*Mar 27 07:01:06.090: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:06.114: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/45
*Mar 27 07:01:06.145: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:06.167: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/16
*Mar 27 07:01:06.200: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:06.226: %HA_EM-6-LOG: catchall: interface TwentyFiveGigE1/1/1
*Mar 27 07:01:06.253: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:06.282: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/25
*Mar 27 07:01:06.317: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:06.347: %HA_EM-6-LOG: catchall: interface TenGigabitEthernet1/1/8
*Mar 27 07:01:06.387: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:06.411: %HA_EM-6-LOG: catchall: interface GigabitEthernet0/0
*Mar 27 07:01:06.474: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/20
*Mar 27 07:01:06.513: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:06.531: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/44
*Mar 27 07:01:06.563: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:06.572: %HA_EM-6-LOG: catchall: interface TwentyFiveGigE1/1/2
*Mar 27 07:01:06.596: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:06.618: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/22
*Mar 27 07:01:06.655: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:06.681: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/1/2
*Mar 27 07:01:06.713: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:06.736: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/3
*Mar 27 07:01:06.770: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:06.794: %HA_EM-6-LOG: catchall: interface TenGigabitEthernet1/1/2
*Mar 27 07:01:06.827: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:06.855: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/46
*Mar 27 07:01:06.888: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:06.915: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/27
*Mar 27 07:01:06.949: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:06.973: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/12
*Mar 27 07:01:07.002: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:07.026: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/33
*Mar 27 07:01:07.059: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:07.068: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/15
*Mar 27 07:01:07.091: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:07.115: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/1/1
*Mar 27 07:01:07.149: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:07.172: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/24
*Mar 27 07:01:07.205: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:07.235: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/4
*Mar 27 07:01:07.269: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:07.303: %HA_EM-6-LOG: catchall: interface FortyGigabitEthernet1/1/1
*Mar 27 07:01:07.336: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:07.366: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/21
*Mar 27 07:01:07.396: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:07.419: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/31
*Mar 27 07:01:07.450: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:07.478: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/11
*Mar 27 07:01:07.510: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:07.540: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/36
*Mar 27 07:01:07.569: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:07.581: %HA_EM-6-LOG: catchall: interface TenGigabitEthernet1/1/6
*Mar 27 07:01:07.618: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:07.640: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/30
*Mar 27 07:01:07.676: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:07.700: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/7
*Mar 27 07:01:07.732: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:07.756: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/23
*Mar 27 07:01:07.789: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:07.814: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/6
*Mar 27 07:01:07.849: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:07.871: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/9
*Mar 27 07:01:07.902: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:07.929: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/28
*Mar 27 07:01:07.965: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:07.996: %HA_EM-6-LOG: catchall: interface TenGigabitEthernet1/1/1
*Mar 27 07:01:08.029: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:08.060: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/18
*Mar 27 07:01:08.074: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:08.093: %HA_EM-6-LOG: catchall: interface TenGigabitEthernet1/1/4
*Mar 27 07:01:08.125: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:08.154: %HA_EM-6-LOG: catchall: interface TenGigabitEthernet1/1/5
*Mar 27 07:01:08.183: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:08.208: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/37
*Mar 27 07:01:08.246: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:08.272: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/35
*Mar 27 07:01:08.306: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:08.326: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/13
*Mar 27 07:01:08.362: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:08.389: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/38
*Mar 27 07:01:08.424: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:08.457: %HA_EM-6-LOG: catchall: interface FortyGigabitEthernet1/1/2
*Mar 27 07:01:08.493: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:08.519: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/1/4
*Mar 27 07:01:08.553: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:08.569: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/1
*Mar 27 07:01:08.600: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:08.629: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/5
*Mar 27 07:01:08.662: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:08.690: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/48
*Mar 27 07:01:08.722: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:08.750: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/40
*Mar 27 07:01:08.783: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:08.804: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/34
*Mar 27 07:01:08.839: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:08.868: %HA_EM-6-LOG: catchall: interface TenGigabitEthernet1/1/7
*Mar 27 07:01:08.906: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:08.932: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/19
*Mar 27 07:01:08.967: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:08.991: %HA_EM-6-LOG: catchall: interface TenGigabitEthernet1/1/3
*Mar 27 07:01:09.026: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:09.052: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/10
*Mar 27 07:01:09.071: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:09.087: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/26
*Mar 27 07:01:09.119: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:09.145: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/2
*Mar 27 07:01:09.180: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:09.207: %HA_EM-6-LOG: catchall: interface GigabitEthernet1/0/17
*Mar 27 07:01:09.241: %HA_EM-6-LOG: catchall: device-tracking attach-policy IPDT_MAX_10
*Mar 27 07:01:09.244: %HA_EM-6-LOG: catchall: exit
*Mar 27 07:01:09.249: %SYS-5-CONFIG_I: Configured from console by dnac on vty3 (10.0.0.101)
*Mar 27 07:01:09.250: %HA_EM-6-LOG: catchall: exit
*Mar 27 07:01:09.252: %HA_EM-6-LOG: catchall: exit
*Mar 27 07:01:09.454: %SEC_LOGIN-5-LOGIN_SUCCESS: Login Success [user: dnac] [Source: 10.0.0.101] [localport: 22] at 07:01:09 UTC Fri Mar 27 2020
*Mar 27 07:01:09.466: %HA_EM-6-LOG: catchall: enable
*Mar 27 07:01:09.473: %HA_EM-6-LOG: catchall: terminal length 0
*Mar 27 07:01:09.490: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 07:01:09.509: %HA_EM-6-LOG: catchall: write memory
*Mar 27 07:01:10.051: %HA_EM-6-LOG: catchall: copy flash:vlan.dat https:
*Mar 27 07:01:10.102: %HA_EM-6-LOG: catchall: disable
*Mar 27 07:01:10.625: %SEC_LOGIN-5-LOGIN_SUCCESS: Login Success [user: dnac] [Source: 10.0.0.101] [localport: 22] at 07:01:10 UTC Fri Mar 27 2020
*Mar 27 07:01:10.637: %HA_EM-6-LOG: catchall: enable
*Mar 27 07:01:10.651: %HA_EM-6-LOG: catchall: terminal length 0
*Mar 27 07:01:10.671: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 07:01:10.692: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 07:01:10.701: %HA_EM-6-LOG: catchall: configure terminal
*Mar 27 07:01:10.734: %HA_EM-6-LOG: catchall: ip http client source-interface Vlan1
*Mar 27 07:01:10.762: %HA_EM-6-LOG: catchall: ip ssh source-interface Vlan1
*Mar 27 07:01:10.779: %HA_EM-6-LOG: catchall: ip ssh version 2
*Mar 27 07:01:10.797: %HA_EM-6-LOG: catchall: ip domain lookup
*Mar 27 07:01:10.820: %HA_EM-6-LOG: catchall: crypto pki trustpoint DNAC-CA
*Mar 27 07:01:10.843: %HA_EM-6-LOG: catchall: source interface Vlan1
*Mar 27 07:01:10.868: %HA_EM-6-LOG: catchall: enrollment mode ra
*Mar 27 07:01:10.893: %HA_EM-6-LOG: catchall: enrollment terminal
*Mar 27 07:01:10.924: %HA_EM-6-LOG: catchall: usage ssl-client
*Mar 27 07:01:10.943: %HA_EM-6-LOG: catchall: revocation-check crl none
*Mar 27 07:01:10.952: %HA_EM-6-LOG: catchall: exit
*Mar 27 07:01:10.976: %HA_EM-6-LOG: catchall: crypto pki authenticate DNAC-CA
*Mar 27 07:01:11.967: %SYS-5-CONFIG_I: Configured from console by dnac on vty3 (10.0.0.101)
*Mar 27 07:01:11.968: %HA_EM-6-LOG: catchall: exit
*Mar 27 07:01:19.576: %HA_EM-6-LOG: catchall: show platform software process list switch active R0 name wncd_0
*Mar 27 07:01:19.894: %HA_EM-6-LOG: catchall: show hosts
*Mar 27 07:01:19.921: %HA_EM-6-LOG: catchall: show running-config
*Mar 27 07:01:20.196: %HA_EM-6-LOG: catchall: show clock
*Mar 27 07:01:20.252: %HA_EM-6-LOG: catchall: show crypto pki certificates
*Mar 27 07:01:20.297: %HA_EM-6-LOG: catchall: show version
C9300#
In short this is what happens:
- show running-config
- Various show commands to collect specific information
- The trustpoint DNAC-CA is deleted along with any RSA key pairs of the DNAC-CA label
- IPDT is enabled and configured for all interfaces
- Source interface for HTTP and SSH is configured
- SSH version 2 is configured
- Domain lookups are enabled
- DNAC certificate is installed using the DNAC-CA trustpoint
Note that this happens because, by default, the Device Controllability is enabled. The exact section of the documentation related to this configuration is this:
- Device in Inventory: After a successful initial inventory collection, IPDT and controller certificates are configured on devices.
Now that the device has been added to the inventory, we can move on and take a look at what happens when we provision various settings found under the Design - Network section of DNAC. To provision these settings you must go to Provision and select the device, choose Actions - Provision - Provision Device:
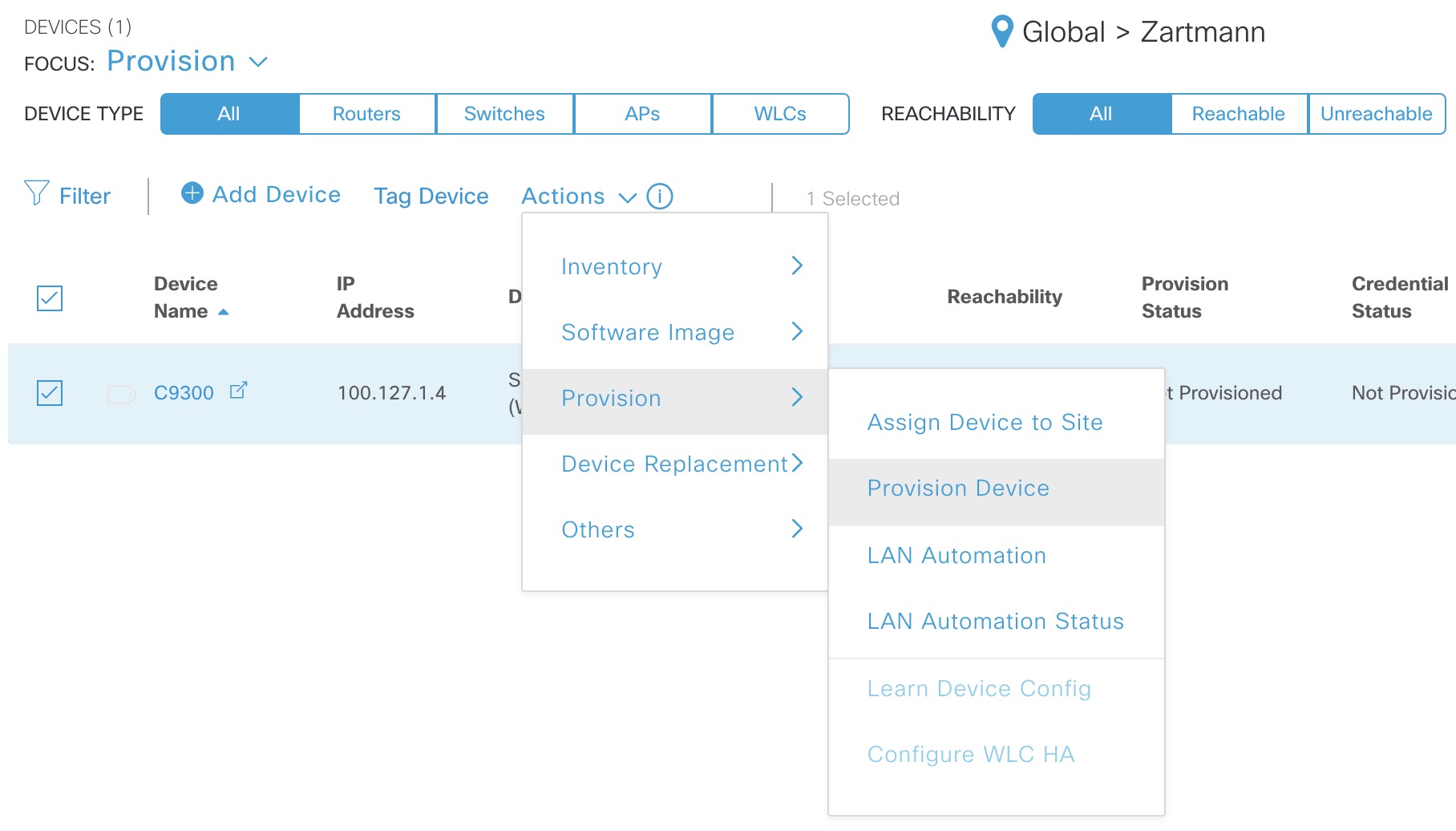
AAA Server - Network - TACACS+
Starting from the top of the network settings page, we have AAA Servers. This DNAC has already been integrated with ISE, hence we can set up TACACS+ for device management. This is refered to as the “Network” portion of the AAA servers:
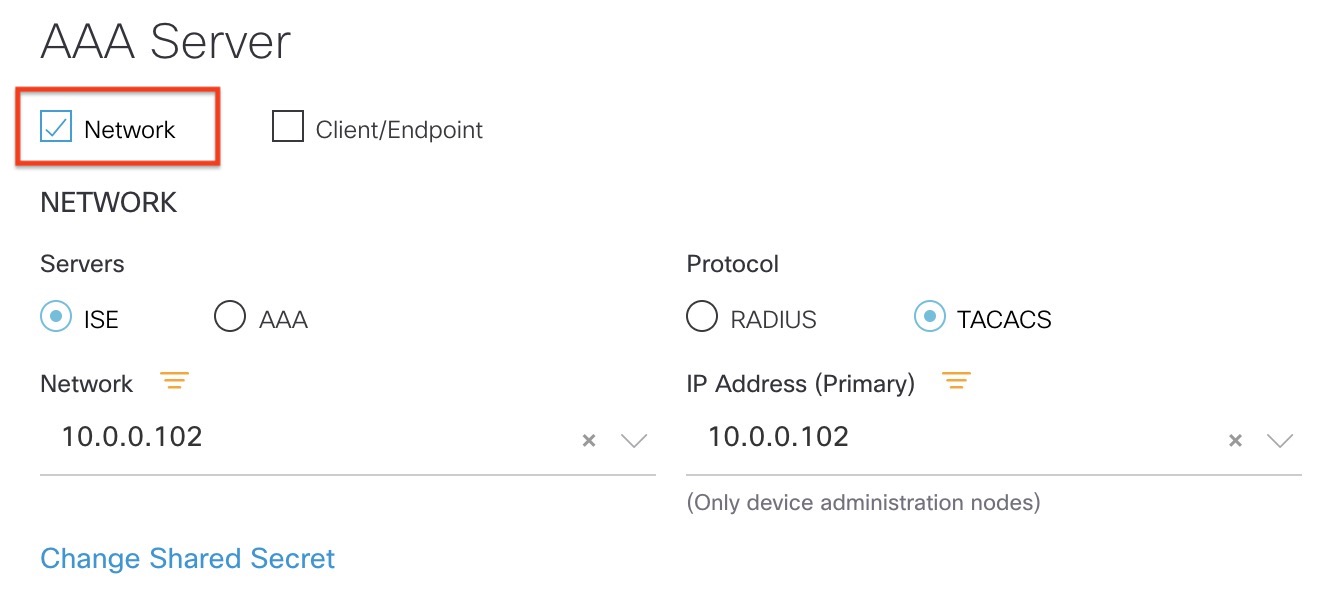
When we provision a device in DNAC, a breif summary of the settings is shown on the last page of the provision wizard:
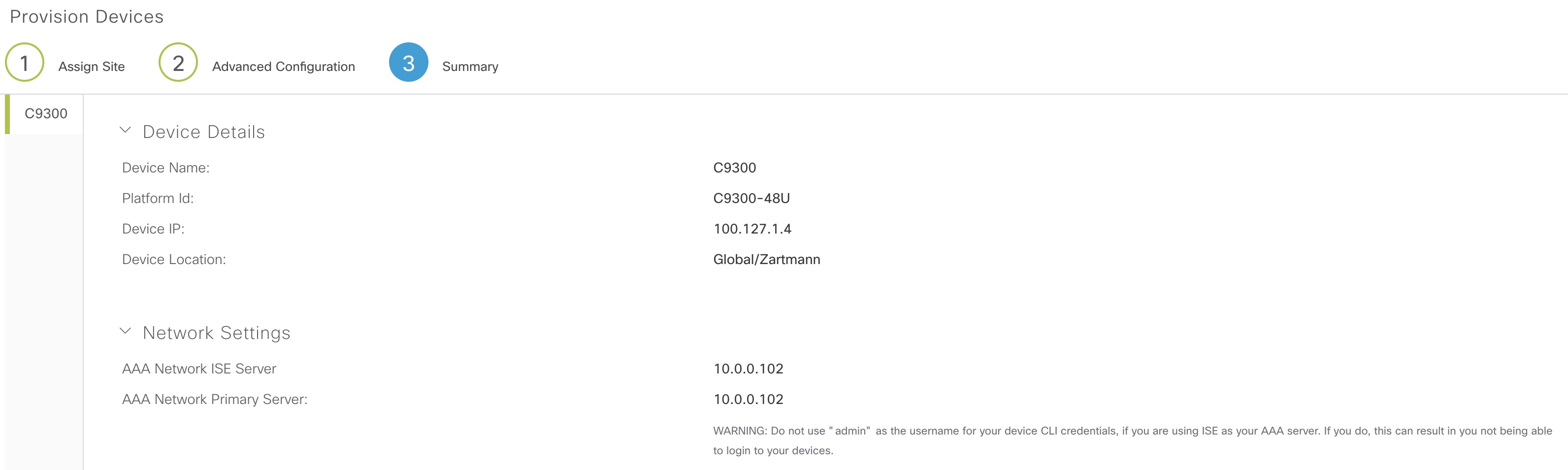
Let’s see what happens when we provision the device using this network setting:
*Mar 27 08:18:19.660: %HA_EM-6-LOG: catchall: enable
*Mar 27 08:18:19.672: %HA_EM-6-LOG: catchall: terminal length 0
*Mar 27 08:18:19.688: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 08:18:19.722: %HA_EM-6-LOG: catchall: authentication display config-mode
*Mar 27 08:18:20.132: %HA_EM-6-LOG: catchall: show running-config
*Mar 27 08:18:20.542: %SEC_LOGIN-5-LOGIN_SUCCESS: Login Success [user: dnac] [Source: 10.0.0.101] [localport: 22] at 08:18:20 UTC Fri Mar 27 2020
*Mar 27 08:18:20.551: %HA_EM-6-LOG: catchall: enable
*Mar 27 08:18:20.564: %HA_EM-6-LOG: catchall: terminal length 0
*Mar 27 08:18:20.570: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 08:18:20.573: %HA_EM-6-LOG: catchall: configure terminal
*Mar 27 08:18:20.593: %HA_EM-6-LOG: catchall: authentication convert-to new-style
*Mar 27 08:18:20.611: %HA_EM-6-LOG: catchall: no ip domain name
*Mar 27 08:18:20.628: %HA_EM-6-LOG: catchall: no ip name-server
*Mar 27 08:18:20.657: %HA_EM-6-LOG: catchall: ip tacacs source-interface Vlan1
*Mar 27 08:18:20.674: %HA_EM-6-LOG: catchall: aaa new-model
*Mar 27 08:18:20.694: %HA_EM-6-LOG: catchall: aaa session-id common
*Mar 27 08:18:20.721: %HA_EM-6-LOG: catchall: tacacs server dnac-tacacs_10.0.0.102
*Mar 27 08:18:20.739: %HA_EM-6-LOG: catchall: address ipv4 10.0.0.102
*Mar 27 08:18:20.745: %AAAA-4-CLI_DEPRECATED: WARNING: Command has been added to the configuration using a type 0 password. However, type 0 passwords will soon be deprecated. Migrate to a supported password type
*Mar 27 08:18:20.745: %AAAA-4-CLI_DEPRECATED: WARNING: Command has been added to the configuration using a type 0 password. However, type 0 passwords will soon be deprecated. Migrate to a supported password type
*Mar 27 08:18:20.748: %HA_EM-6-LOG: catchall: key <secret>
*Mar 27 08:18:20.750: %HA_EM-6-LOG: catchall: timeout 4
*Mar 27 08:18:20.755: %HA_EM-6-LOG: catchall: exit
*Mar 27 08:18:20.785: %HA_EM-6-LOG: catchall: tacacs server dnac-tacacs_10.0.0.102
*Mar 27 08:18:20.802: %HA_EM-6-LOG: catchall: address ipv4 10.0.0.102
*Mar 27 08:18:20.805: %AAAA-4-CLI_DEPRECATED: WARNING: Command has been added to the configuration using a type 0 password. However, type 0 passwords will soon be deprecated. Migrate to a supported password type
*Mar 27 08:18:20.805: %AAAA-4-CLI_DEPRECATED: WARNING: Command has been added to the configuration using a type 0 password. However, type 0 passwords will soon be deprecated. Migrate to a supported password type
*Mar 27 08:18:20.808: %HA_EM-6-LOG: catchall: key <secret>
*Mar 27 08:18:20.819: %HA_EM-6-LOG: catchall: timeout 4
*Mar 27 08:18:20.824: %HA_EM-6-LOG: catchall: exit
*Mar 27 08:18:20.868: %HA_EM-6-LOG: catchall: aaa group server tacacs+ dnac-network-tacacs-group
*Mar 27 08:18:20.895: %HA_EM-6-LOG: catchall: server name dnac-tacacs_10.0.0.102
*Mar 27 08:18:20.901: %HA_EM-6-LOG: catchall: exit
*Mar 27 08:18:20.936: %HA_EM-6-LOG: catchall: aaa group server tacacs+ dnac-network-tacacs-group
*Mar 27 08:18:20.967: %HA_EM-6-LOG: catchall: server name dnac-tacacs_10.0.0.102
*Mar 27 08:18:20.973: %HA_EM-6-LOG: catchall: exit
*Mar 27 08:18:21.028: %HA_EM-6-LOG: catchall: aaa accounting exec default start-stop group dnac-network-tacacs-group
*Mar 27 08:18:21.062: %HA_EM-6-LOG: catchall: aaa accounting update newinfo periodic 2880
*Mar 27 08:18:21.073: %HA_EM-6-LOG: catchall: aaa authorization exec default local
*Mar 27 08:18:21.137: %HA_EM-6-LOG: catchall: aaa authorization exec VTY_author group dnac-network-tacacs-group local if-authenticated
*Mar 27 08:18:21.163: %HA_EM-6-LOG: catchall: aaa authentication login default local
*Mar 27 08:18:21.210: %HA_EM-6-LOG: catchall: aaa authentication login VTY_authen group dnac-network-tacacs-group local
*Mar 27 08:18:21.231: %HA_EM-6-LOG: catchall: dot1x system-auth-control
*Mar 27 08:18:21.258: %HA_EM-6-LOG: catchall: radius-server vsa send authentication
*Mar 27 08:18:21.286: %HA_EM-6-LOG: catchall: radius-server vsa send accounting
*Mar 27 08:18:21.319: %HA_EM-6-LOG: catchall: radius-server dead-criteria time 5 tries 3
*Mar 27 08:18:21.338: %HA_EM-6-LOG: catchall: radius-server deadtime 3
*Mar 27 08:18:21.374: %HA_EM-6-LOG: catchall: radius-server attribute 31 mac format ietf upper-case
*Mar 27 08:18:21.418: %HA_EM-6-LOG: catchall: radius-server attribute 31 send nas-port-detail mac-only
*Mar 27 08:18:21.464: %HA_EM-6-LOG: catchall: radius-server attribute 25 access-request include
*Mar 27 08:18:21.495: %HA_EM-6-LOG: catchall: radius-server attribute 8 include-in-access-req
*Mar 27 08:18:21.529: %HA_EM-6-LOG: catchall: radius-server attribute 6 on-for-login-auth
*Mar 27 08:18:21.564: %HA_EM-6-LOG: catchall: radius-server attribute 6 support-multiple
*Mar 27 08:18:21.570: %HA_EM-6-LOG: catchall: line vty 0 15
*Mar 27 08:18:21.582: %HA_EM-6-LOG: catchall: login authentication VTY_authen
*Mar 27 08:18:21.604: %HA_EM-6-LOG: catchall: authorization exec VTY_author
*Mar 27 08:18:21.617: %HA_EM-6-LOG: catchall: transport input all
*Mar 27 08:18:21.639: %HA_EM-6-LOG: catchall: ntp source Vlan1
*Mar 27 08:18:21.655: %HA_EM-6-LOG: catchall: ip domain lookup
*Mar 27 08:18:21.677: %HA_EM-6-LOG: catchall: service password-encryption
*Mar 27 08:18:21.681: %SYS-5-CONFIG_I: Configured from console by dnac on vty1 (10.0.0.101)
*Mar 27 08:18:21.683: %HA_EM-6-LOG: catchall: end
*Mar 27 08:18:21.699: %HA_EM-6-LOG: catchall: write memory
*Mar 27 08:18:24.491: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 08:18:24.505: %HA_EM-6-LOG: catchall: configure terminal
*Mar 27 08:18:24.511: %SYS-5-CONFIG_I: Configured from console by dnac on vty0 (10.0.0.101)
Many things happen here. In the beginning DNAC takes a look at the authentication mode. In this scenario DNAC converts to the new-style (IBNS 2.0) mode. Here is a list of what’s going on:
- Domain name and servers are un-configured!
- TACACS+ configurations are pushed
- The TACACS+ server is configured twice!
- Two AAA method lists are created
- VTY_author
- VTY_authen
- RADIUS settings are configured!
- VTY lines are configured
- AAA method lists are applied
- Transport for ALL input is configured!
- NTP source is configured
- Domain lookup enabled
- Service password-encryption enabled
Funny enough the TACACS+ server is configured twice even though i only have one PSN! Although I didn’t configure any NTP settings, the source interface is configured for NTP! Domain lookups are enabled once again along with service password encryption which is always a good idaa.
What doesn’t make any sense in the above configurations are the radius-server parts. I didn’t specify any radius settings at all, yet DNAC configures these settings!
AAA Servers - Client/Endpoint - RADIUS
If we want to configure 802.1x we need a radius server. This setting enables us to prepare for 802.1x implementations.
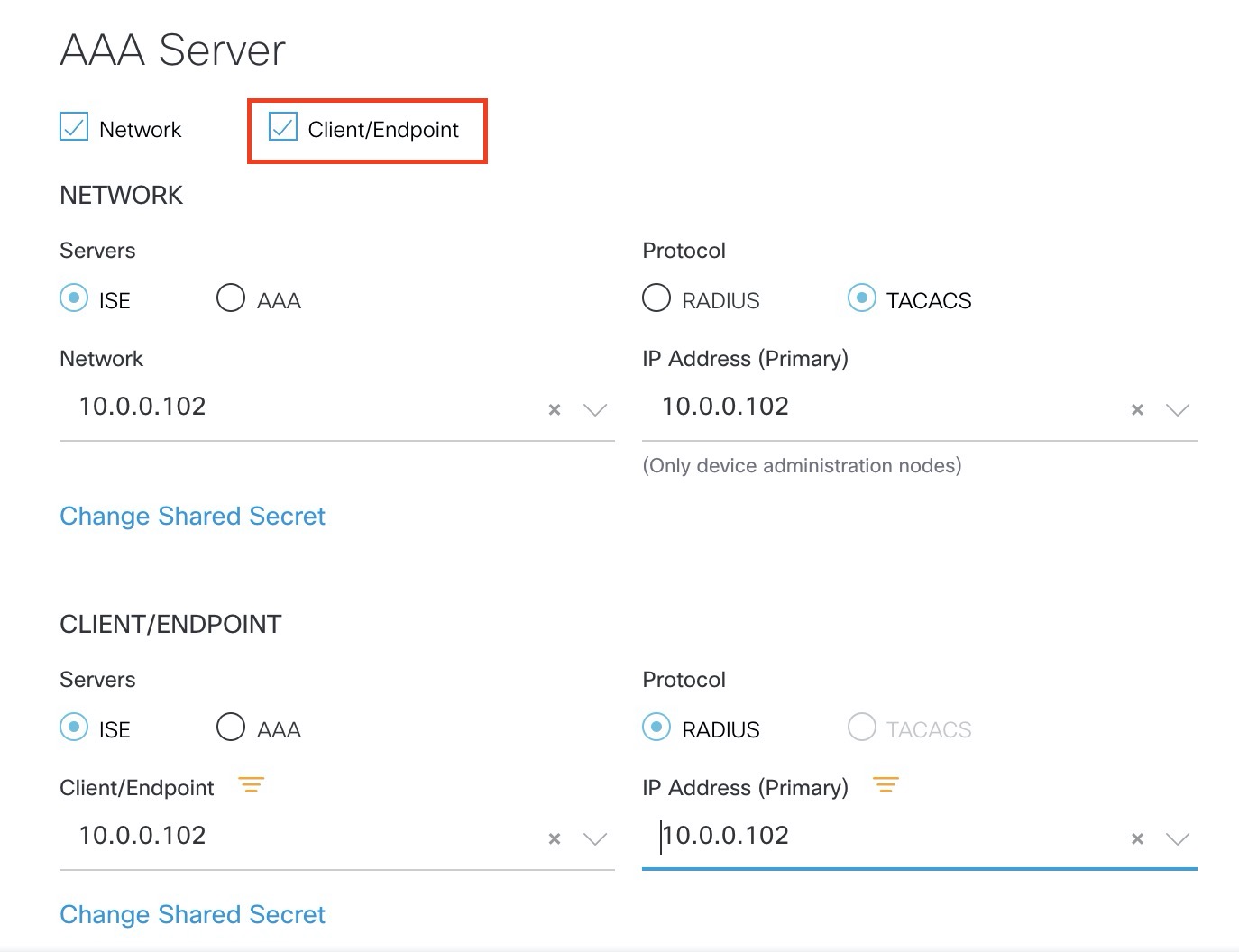
Let’s see what happens upon provisioning:
C9300#
*Mar 27 09:38:58.360: %SEC_LOGIN-5-LOGIN_SUCCESS: Login Success [user: dnac] [Source: 10.0.0.101] [localport: 22] at 09:38:58 UTC Fri Mar 27 2020
*Mar 27 09:38:58.380: %HA_EM-6-LOG: catchall: enable
*Mar 27 09:38:58.392: %HA_EM-6-LOG: catchall: terminal length 0
*Mar 27 09:38:58.408: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 09:38:58.439: %HA_EM-6-LOG: catchall: authentication display config-mode
*Mar 27 09:38:58.910: %HA_EM-6-LOG: catchall: show running-config
*Mar 27 09:38:59.307: %SEC_LOGIN-5-LOGIN_SUCCESS: Login Success [user: dnac] [Source: 10.0.0.101] [localport: 22] at 09:38:59 UTC Fri Mar 27 2020
*Mar 27 09:38:59.324: %HA_EM-6-LOG: catchall: enable
*Mar 27 09:38:59.336: %HA_EM-6-LOG: catchall: terminal length 0
*Mar 27 09:38:59.352: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 09:38:59.364: %HA_EM-6-LOG: catchall: configure terminal
*Mar 27 09:38:59.381: %HA_EM-6-LOG: catchall: no ip domain name
*Mar 27 09:38:59.399: %HA_EM-6-LOG: catchall: no ip name-server
*Mar 27 09:38:59.427: %HA_EM-6-LOG: catchall: ip tacacs source-interface Vlan1
*Mar 27 09:38:59.456: %HA_EM-6-LOG: catchall: ip radius source-interface Vlan1
*Mar 27 09:38:59.484: %HA_EM-6-LOG: catchall: ip http max-connections 16
*Mar 27 09:38:59.518: %HA_EM-6-LOG: catchall: ip access-list extended ACL_WEBAUTH_REDIRECT
*Mar 27 09:38:59.541: %HA_EM-6-LOG: catchall: 500 permit tcp any any eq www
*Mar 27 09:38:59.568: %HA_EM-6-LOG: catchall: 600 permit tcp any any eq 443
*Mar 27 09:38:59.575: %HA_EM-6-LOG: catchall: 700 permit tcp any any eq 8443
*Mar 27 09:38:59.606: %HA_EM-6-LOG: catchall: 30 deny ip any host 10.0.0.102
*Mar 27 09:38:59.633: %HA_EM-6-LOG: catchall: 800 deny udp any any eq domain
*Mar 27 09:38:59.667: %HA_EM-6-LOG: catchall: 900 deny udp any eq bootpc any eq bootps
*Mar 27 09:38:59.675: %HA_EM-6-LOG: catchall: exit
*Mar 27 09:38:59.706: %HA_EM-6-LOG: catchall: tacacs server dnac-tacacs_10.0.0.102
*Mar 27 09:38:59.712: %HA_EM-6-LOG: catchall: no timeout
*Mar 27 09:38:59.739: %HA_EM-6-LOG: catchall: no address
*Mar 27 09:38:59.768: %HA_EM-6-LOG: catchall: tacacs server dnac-tacacs_10.0.0.102
*Mar 27 09:38:59.786: %HA_EM-6-LOG: catchall: address ipv4 10.0.0.102
*Mar 27 09:38:59.797: %AAAA-4-CLI_DEPRECATED: WARNING: Command has been added to the configuration using a type 0 password. However, type 0 passwords will soon be deprecated. Migrate to a supported password type
*Mar 27 09:38:59.797: %AAAA-4-CLI_DEPRECATED: WARNING: Command has been added to the configuration using a type 0 password. However, type 0 passwords will soon be deprecated. Migrate to a supported password type
*Mar 27 09:38:59.800: %HA_EM-6-LOG: catchall: key <secret>
*Mar 27 09:38:59.808: %HA_EM-6-LOG: catchall: timeout 4
*Mar 27 09:38:59.817: %HA_EM-6-LOG: catchall: exit
*Mar 27 09:38:59.852: %HA_EM-6-LOG: catchall: tacacs server dnac-tacacs_10.0.0.102
*Mar 27 09:38:59.867: %HA_EM-6-LOG: catchall: no timeout
*Mar 27 09:38:59.885: %HA_EM-6-LOG: catchall: no address
*Mar 27 09:38:59.912: %HA_EM-6-LOG: catchall: tacacs server dnac-tacacs_10.0.0.102
*Mar 27 09:38:59.936: %HA_EM-6-LOG: catchall: address ipv4 10.0.0.102
*Mar 27 09:38:59.951: %AAAA-4-CLI_DEPRECATED: WARNING: Command has been added to the configuration using a type 0 password. However, type 0 passwords will soon be deprecated. Migrate to a supported password type
*Mar 27 09:38:59.951: %AAAA-4-CLI_DEPRECATED: WARNING: Command has been added to the configuration using a type 0 password. However, type 0 passwords will soon be deprecated. Migrate to a supported password type
*Mar 27 09:38:59.953: %HA_EM-6-LOG: catchall: key <secret>
*Mar 27 09:38:59.966: %HA_EM-6-LOG: catchall: timeout 4
*Mar 27 09:38:59.972: %HA_EM-6-LOG: catchall: exit
*Mar 27 09:39:00.013: %HA_EM-6-LOG: catchall: aaa group server radius dnac-client-radius-group
*Mar 27 09:39:00.043: %RADIUS-4-NOSERVNAME: Warning: Server dnac-radius_10.0.0.102 is not defined.
*Mar 27 09:39:00.045: %HA_EM-6-LOG: catchall: server name dnac-radius_10.0.0.102
*Mar 27 09:39:00.059: %HA_EM-6-LOG: catchall: ip radius source-interface Vlan1
*Mar 27 09:39:00.065: %HA_EM-6-LOG: catchall: exit
*Mar 27 09:39:00.089: %HA_EM-6-LOG: catchall: aaa group server tacacs+ dnac-network-tacacs-group
*Mar 27 09:39:00.119: %HA_EM-6-LOG: catchall: server name dnac-tacacs_10.0.0.102
*Mar 27 09:39:00.126: %HA_EM-6-LOG: catchall: exit
*Mar 27 09:39:00.171: %HA_EM-6-LOG: catchall: aaa group server tacacs+ dnac-network-tacacs-group
*Mar 27 09:39:00.202: %HA_EM-6-LOG: catchall: server name dnac-tacacs_10.0.0.102
*Mar 27 09:39:00.206: %HA_EM-6-LOG: catchall: exit
*Mar 27 09:39:00.274: %HA_EM-6-LOG: catchall: aaa accounting identity default start-stop group dnac-client-radius-group
*Mar 27 09:39:00.331: %HA_EM-6-LOG: catchall: aaa authorization network default group dnac-client-radius-group
*Mar 27 09:39:00.398: %HA_EM-6-LOG: catchall: aaa authorization network dnac-cts-list group dnac-client-radius-group
*Mar 27 09:39:00.451: %HA_EM-6-LOG: catchall: aaa authentication dot1x default group dnac-client-radius-group
*Mar 27 09:39:00.520: %HA_EM-6-LOG: catchall: aaa authentication login dnac-cts-list group dnac-client-radius-group local
*Mar 27 09:39:00.554: %HA_EM-6-LOG: catchall: radius server dnac-radius_10.0.0.102
*Mar 27 09:39:00.574: %HA_EM-6-LOG: catchall: address ipv4 10.0.0.102 auth-port 1812 acct-port 1813
*Mar 27 09:39:00.578: %AAAA-4-CLI_DEPRECATED: WARNING: Command has been added to the configuration using a type 0 password. However, type 0 passwords will soon be deprecated. Migrate to a supported password type
*Mar 27 09:39:00.580: %HA_EM-6-LOG: catchall: pac key <secret>
*Mar 27 09:39:00.587: %HA_EM-6-LOG: catchall: retransmit 3
*Mar 27 09:39:00.600: %HA_EM-6-LOG: catchall: timeout 4
*Mar 27 09:39:00.603: Request successfully sent to PAC Provisioning driver.
*Mar 27 09:39:00.605: %HA_EM-6-LOG: catchall: exit
*Mar 27 09:39:00.635: %HA_EM-6-LOG: catchall: radius-server vsa send authentication
*Mar 27 09:39:00.660: %HA_EM-6-LOG: catchall: radius-server vsa send accounting
*Mar 27 09:39:00.693: %HA_EM-6-LOG: catchall: cts authorization list dnac-cts-list
*Mar 27 09:39:00.707: %HA_EM-6-LOG: catchall: line vty 0 15
*Mar 27 09:39:00.734: %HA_EM-6-LOG: catchall: login authentication VTY_authen
*Mar 27 09:39:00.762: %HA_EM-6-LOG: catchall: authorization exec VTY_author
*Mar 27 09:39:00.779: %HA_EM-6-LOG: catchall: transport input all
*Mar 27 09:39:00.805: %HA_EM-6-LOG: catchall: aaa server radius dynamic-author
*Mar 27 09:39:00.832: %AAAA-4-CLI_DEPRECATED: WARNING: Command has been added to the configuration using a type 0 password. However, type 0 passwords will soon be deprecated. Migrate to a supported password type
*Mar 27 09:39:00.834: %HA_EM-6-LOG: catchall: client 10.0.0.102 server-key <secret>
*Mar 27 09:39:00.857: %AAAA-4-CLI_DEPRECATED: WARNING: Command has been added to the configuration using a type 0 password. However, type 0 passwords will soon be deprecated. Migrate to a supported password type
*Mar 27 09:39:00.860: %HA_EM-6-LOG: catchall: client 10.0.0.102 server-key <secret>
*Mar 27 09:39:00.893: %AAAA-4-CLI_DEPRECATED: WARNING: Command has been added to the configuration using a type 0 password. However, type 0 passwords will soon be deprecated. Migrate to a supported password type
*Mar 27 09:39:00.896: %HA_EM-6-LOG: catchall: client 10.0.0.102 server-key <secret>
*Mar 27 09:39:00.899: %HA_EM-6-LOG: catchall: exit
*Mar 27 09:39:00.912: %HA_EM-6-LOG: catchall: ip domain lookup
*Mar 27 09:39:00.917: %SYS-5-CONFIG_I: Configured from console by dnac on vty2 (10.0.0.101)
*Mar 27 09:39:00.919: %HA_EM-6-LOG: catchall: end
*Mar 27 09:39:00.937: %HA_EM-6-LOG: catchall: write memory
*Mar 27 09:39:28.941: %RADIUS-3-ALLDEADSERVER: Group dnac-client-radius-group: No active radius servers found. Id 1.
*Mar 27 09:40:28.942: %CTS-3-AAA_NO_RADIUS_SERVER: No RADIUS servers available for CTS AAA request for CTS env-data SM
*Mar 27 09:41:02.602: %HA_EM-6-LOG: catchall: disable
*Mar 27 09:41:02.605: %HA_EM-6-LOG: catchall: disable
*Mar 27 09:41:02.615: %HA_EM-6-LOG: catchall: connect out
*Mar 27 09:41:02.617: %SYS-6-LOGOUT: User dnac has exited tty session 2(10.0.0.101)
*Mar 27 09:42:12.819: %RADIUS-6-SERVERALIVE: Group dnac-client-radius-group: Radius server 10.0.0.102:1812,1813 is responding again (previously dead).
*Mar 27 09:42:12.819: %RADIUS-4-RADIUS_ALIVE: RADIUS server 10.0.0.102:1812,1813 is being marked alive.
*Mar 27 09:42:20.192: %HA_EM-6-LOG: catchall: disable
C9300#
A list of things going on above:
- Domain name and servers are un-configured! (Again!)
- Both tacacs and radius souce interface is configured
- TACACS+ server is re-configured
- Radius server is configured
- VTY lines are configured again along with transport for ALL inputs
- Domain lookup enabled again
It looks like DNAC isn’t very adaptive when it comes to knowing what is already configured. It configures many of the same things again. Not very optimal, but it doesn’t hurt anything other than filling up logs with unnecessary information.
DHCP Server
It might seem odd that you would add a DHCP server to network settings as this usually relate to configuring IP helper addresses on SVIs. Defining a DHCP server in the network settings for a site (or global) makes this server appear when configuring IP (pool) reservations thereby saving you time when creating these for SDA.
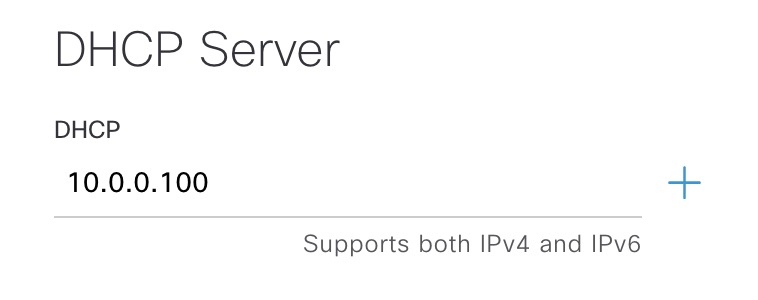
When provisioning the device this will show up in the summary:
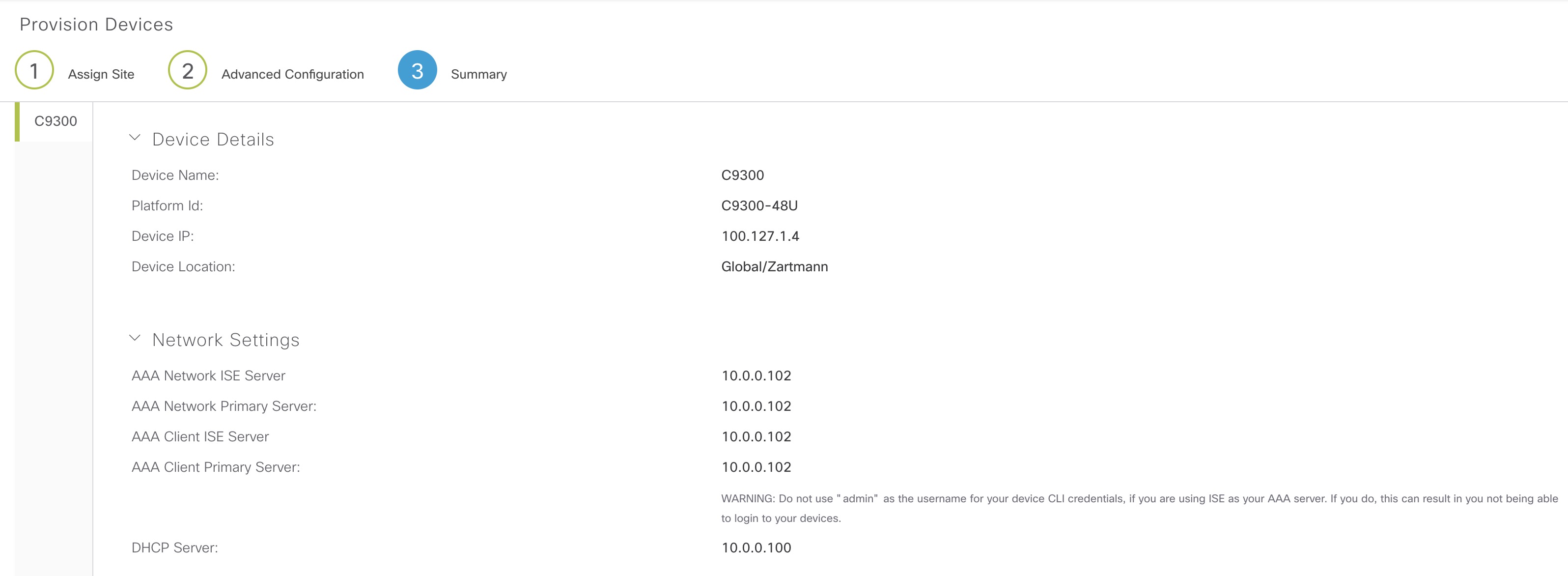
Furtunately DNAC is wise enough to know that it shouldn’t configure anything when only the DHCP server network settings have been modified - at least for this demonstration where SDA isn’t in scope.
DNS Server
Next in the network settings is DNS Server. I’ve added a domain name of zartmann.lab and the DNS server 10.0.0.100:
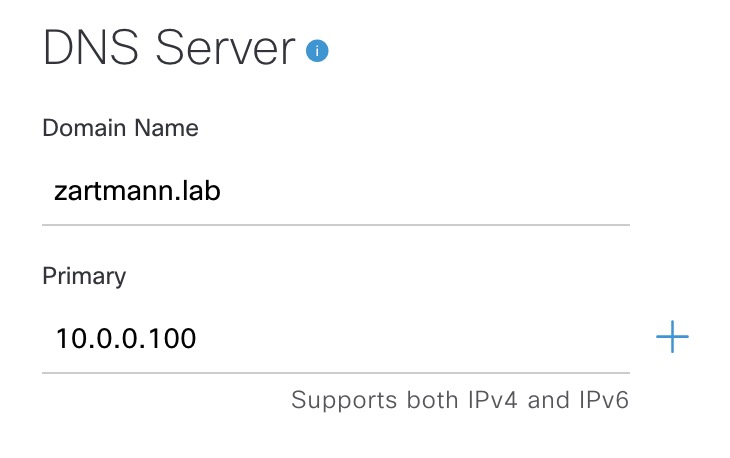
Let’s see what happens when provisioning the device:
C9300#
*Mar 27 12:48:25.183: %SEC_LOGIN-5-LOGIN_SUCCESS: Login Success [user: dnac] [Source: 10.0.0.101] [localport: 22] at 12:48:25 UTC Fri Mar 27 2020
*Mar 27 12:48:25.200: %HA_EM-6-LOG: catchall: enable
*Mar 27 12:48:25.208: %HA_EM-6-LOG: catchall: terminal length 0
*Mar 27 12:48:25.223: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 12:48:25.306: %HA_EM-6-LOG: catchall: show platform software process list switch active R0 name wncd_0
*Mar 27 12:48:25.584: %HA_EM-6-LOG: catchall: show hosts
*Mar 27 12:48:25.612: %HA_EM-6-LOG: catchall: show running-config
*Mar 27 12:48:25.829: %HA_EM-6-LOG: catchall: show clock
*Mar 27 12:48:25.879: %HA_EM-6-LOG: catchall: show version
C9300#
That’s odd. Nothing is configured! This wasn’t my intent at all!
Syslog Server
By default DNAC is selected as syslog server. I’ll add 10.0.0.100 as syslog server:
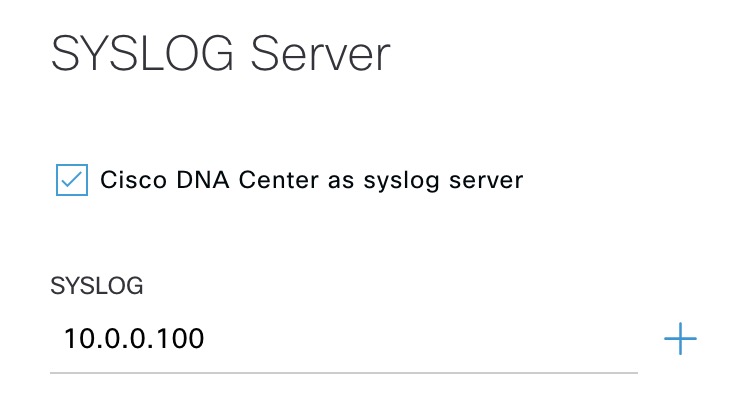
I wanted to go to provision, but saw that DNAC has already configured these settings, meaning that the syslog server is configured without having to do anything at all other than configure the server in network settings. Let’s hope you don’t have a topy when doing so!
C9300#
*Mar 27 12:50:47.544: %SEC_LOGIN-5-LOGIN_SUCCESS: Login Success [user: dnac] [Source: 10.0.0.101] [localport: 22] at 12:50:47 UTC Fri Mar 27 2020
*Mar 27 12:50:47.565: %HA_EM-6-LOG: catchall: enable
*Mar 27 12:50:47.570: %HA_EM-6-LOG: catchall: terminal length 0
*Mar 27 12:50:47.578: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 12:50:47.595: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 12:50:47.610: %HA_EM-6-LOG: catchall: configure terminal
*Mar 27 12:50:47.634: %SYS-6-LOGGINGHOST_STARTSTOP: Logging to host 10.0.0.201 port 514 stopped - CLI initiated
*Mar 27 12:50:47.635: %HA_EM-6-LOG: catchall: no logging host 10.0.0.201
*Mar 27 12:50:47.638: %SYS-5-CONFIG_I: Configured from console by dnac on vty1 (10.0.0.101)
*Mar 27 12:50:48.584: %SYS-6-LOGGINGHOST_STARTSTOP: Logging to host 10.0.0.100 port 0 CLI Request Triggered
*Mar 27 12:50:48.585: %HA_EM-6-LOG: catchall: logging host 10.0.0.100 transport udp port 514
*Mar 27 12:50:48.587: %SYS-6-LOGGINGHOST_STARTSTOP: Logging to host 10.0.0.100 port 514 started - CLI initiated
*Mar 27 12:50:48.619: %SYS-6-LOGGINGHOST_STARTSTOP: Logging to host 10.0.0.201 port 0 CLI Request Triggered
*Mar 27 12:50:48.621: %HA_EM-6-LOG: catchall: logging host 10.0.0.201 transport udp port 514
*Mar 27 12:50:48.622: %SYS-6-LOGGINGHOST_STARTSTOP: Logging to host 10.0.0.201 port 514 started - CLI initiated
*Mar 27 12:50:48.624: %HA_EM-6-LOG: catchall: logging trap 6
*Mar 27 12:50:48.625: %SYS-5-CONFIG_I: Configured from console by dnac on vty1 (10.0.0.101)
*Mar 27 12:50:48.627: %HA_EM-6-LOG: catchall: exit
*Mar 27 12:50:48.733: %HA_EM-6-LOG: catchall: write memory
C9300#
10.0.0.201 is the VIP of this DNAC.
SNMP Server
This setting is kind of weird as no relation to which SNMP version is stated. Let’s try and configure 10.0.0.100 as a SNMP server and see what happens.
Again I saw DNAC configure this setting before I had to provision the device!
C9300#
*Mar 27 12:55:10.021: %SEC_LOGIN-5-LOGIN_SUCCESS: Login Success [user: dnac] [Source: 10.0.0.101] [localport: 22] at 12:55:10 UTC Fri Mar 27 2020
*Mar 27 12:55:10.043: %HA_EM-6-LOG: catchall: enable
*Mar 27 12:55:10.054: %HA_EM-6-LOG: catchall: terminal length 0
*Mar 27 12:55:10.068: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 12:55:10.071: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 12:55:10.077: %HA_EM-6-LOG: catchall: configure terminal
*Mar 27 12:55:10.116: %HA_EM-6-LOG: catchall: no snmp-server host 10.0.0.201 traps dnac
*Mar 27 12:55:10.124: %SYS-5-CONFIG_I: Configured from console by dnac on vty0 (10.0.0.101)
*Mar 27 12:55:10.125: %HA_EM-6-LOG: catchall: exit
*Mar 27 12:55:10.229: %HA_EM-6-LOG: catchall: write memory
*Mar 27 12:55:10.952: %HA_EM-6-LOG: catchall: terminal width 0
*Mar 27 12:55:10.965: %HA_EM-6-LOG: catchall: configure terminal
*Mar 27 12:55:11.066: %HA_EM-6-LOG: catchall: snmp-server host 10.0.0.100 traps version 2c dnac udp-port 162
*Mar 27 12:55:11.133: %HA_EM-6-LOG: catchall: snmp-server enable traps
*Mar 27 12:55:11.235: %HA_EM-6-LOG: catchall: snmp-server host 10.0.0.201 traps version 2c dnac udp-port 162
*Mar 27 12:55:11.320: %HA_EM-6-LOG: catchall: snmp-server enable traps
*Mar 27 12:55:11.329: %SYS-5-CONFIG_I: Configured from console by dnac on vty0 (10.0.0.101)
*Mar 27 12:55:11.331: %HA_EM-6-LOG: catchall: exit
*Mar 27 12:55:11.434: %HA_EM-6-LOG: catchall: write memory
C9300#
It turns out that this setting configures SNMPv2c traps. Currently DNAC only supports SNMPv2c traps for its assurance. If you want anything other than this for traps, you must use Day-N templates and build the configuration yourself.
NTP Server
I’ll configure our usual IP of 10.0.0.100 for NTP server:
This time we must provision the device ourself. But as with the DNS Server setting nothing happens! Not our intent!
Time Zone
The default is UTC. I’ll change it:
Upon provisioning of the device nothing happens!
Message of the day
Last item I’ll demonstrate in the post is the MTOD banner. It is set to not override by default, but I’ll change this:
Like with many of the other settings nothing happens upon provisioning.
Summary
With all the above settings enabled when we provision the device this summary is shown:
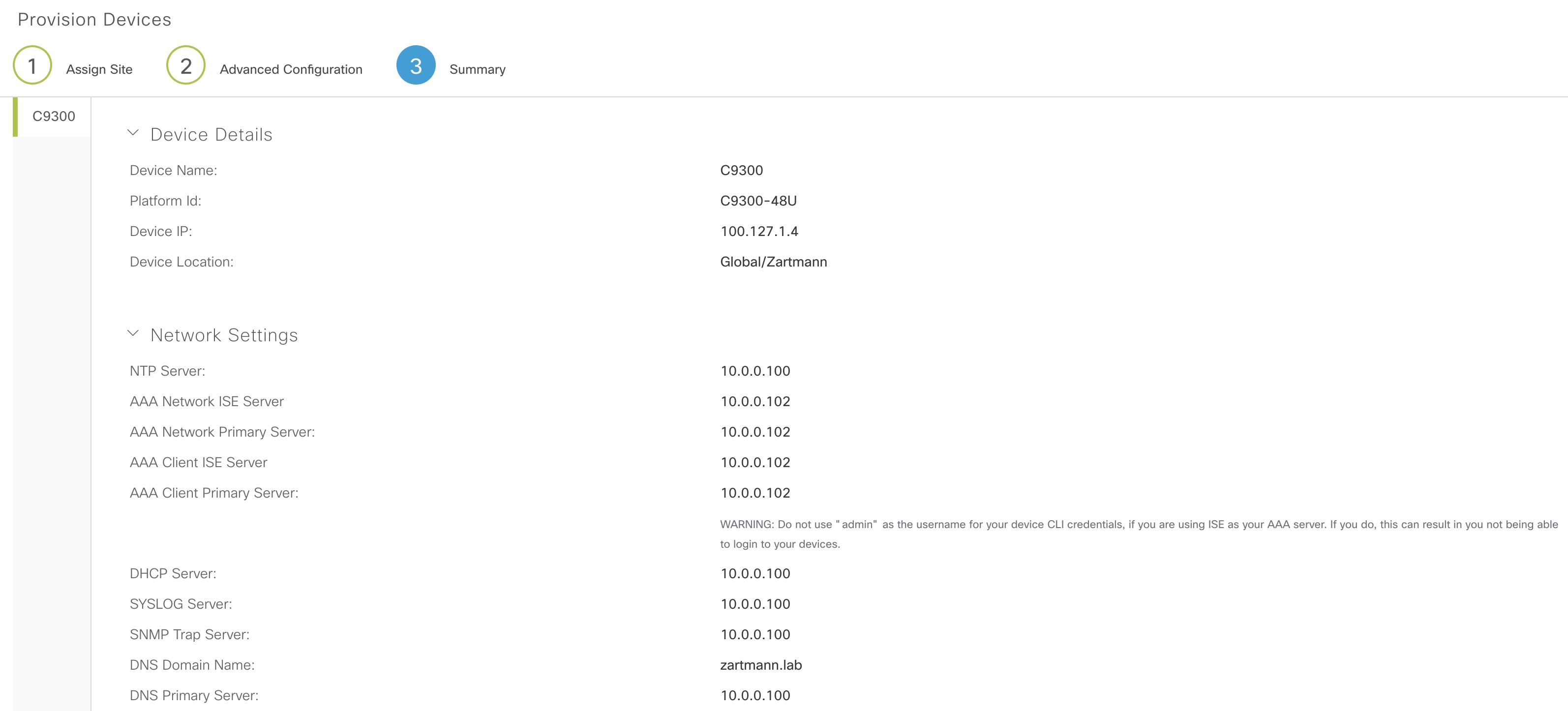
Not all settings are displayed. And as we saw above not all settings are configure upon provisioning.
Conclusion
In this post the various network settings of DNAC were tested with provisioning of a device. It turns out that not all settings get configured upon provisioning. These are:
- DNS Server
- NTP Server
- Message of the day
Some settings are pushed immediately by DNAC. These are:
- Syslog Server
- SNMP Server
It was also revealed that DNAC configures settings that have already been configured with AAA Server settings. And when enabling just TACACS+ for network device administration, some radius settings were configured on the device.
I hope this post was useful to you. Thanks for reading it.
