Security
VACL
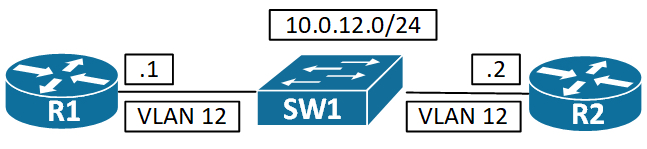
VLAN Access List can be used to filter traffic within a VLAN. A feature that is easily overlooked when troubleshooting connectivity problems at L2. It is configured a bit like a route-map. Let’s have a look at a simple topology to demonstrate how it works:
Say we want to not allow any devices on Vlan 12 to be able to ping each other. We can achieve this using a VACL.
! SW1 VACL to block ICMP: SW1(config)#ip access-list extended ping SW1(config-ext-nacl)#permit icmp any any echo SW1(config-ext-nacl)#exit SW1(config)# SW1(config)#vlan access-map vlan12acl 10 SW1(config-access-map)#match ip address ping SW1(config-access-map)#action drop SW1(config-access-map)#vlan access-map vlan12acl 20 SW1(config-access-map)#action forward SW1(config-access-map)#exit SW1(config)#vlan filter vlan12acl vlan-list 12 SW1(config)#
As always verify your configuration:
! SW1 VACL verification:
SW1#sh vlan filter
VLAN Map vlan12acl is filtering VLANs:
12
SW1#sh vlan access-map
Vlan access-map "vlan12acl" 10
Match clauses:
ip address: ping
Action:
drop
Vlan access-map "vlan12acl" 20
Match clauses:
Action:
forward
SW1#
Now let’s verify that we have achieved our goal by pinging R2 from R1:
! R1 pings R2: R1#ping 10.0.12.2 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.0.12.2, timeout is 2 seconds: ..... Success rate is 0 percent (0/5) R1#sh ip arp Protocol Address Age (min) Hardware Addr Type Interface Internet 10.0.12.1 - aabb.cc00.f000 ARPA Ethernet0/0 Internet 10.0.12.2 0 aabb.cc01.0000 ARPA Ethernet0/0 R1#
It did not work!
! SW1 access-list counter:
SW1#sh access-l ping
Extended IP access list ping
10 permit icmp any any echo (4 matches)
SW1#
We have matches on our ping ACL on SW1.
Notice the configuration of SW1. I used a catch-all sequence to allow all other traffic except the traffic that matches the ACL in sequence 10. I’ve enabled the http server on R1 to demonstrate that the two routers in fact can communicate with each other:
! R2 access web server on R1:
R2#telnet 10.0.12.1 80
Trying 10.0.12.1, 80 ... Open
R2#
! R1 verify the connection from R2:
R1#sh ip http server connection
HTTP server current connections:
local-ipaddress:port remote-ipaddress:port in-bytes out-bytes
10.0.12.1:80 10.0.12.2:15272 2 0
R1#
With VACLs you can match based on:
- IP ACLs
- IPv6 ACLs
- MAC ACLs
And you have two actions in general (some platforms have additional actions like capture and redirect):
- forward
- drop
And remember just like a route-map you have an implicit deny sequence in the end, meaning that you must define a catch-all sequence to forward the rest of the traffic – unless you are doing a restrictive approach where you only allow certain traffic defined and drop the rest.
That’s pretty much all there is to VACLs. Straight forward feature, but a silent killer when troubleshooting.