Campus Segmentation and Beyond
Table of Contents
Security is top of mind for most companies today. And for good reasons. Every day new major security incidents hit both the private and public sectors. We’re no longer dealing with curious geeks, script kiddies, and smaller groups of cyber criminals. Hacking used to be a niche thing. Today state-sponsored hackers are a reality.
Although you cannot guarantee protection from these malicious events, you can try to limit the risk and possibility of their success. Various methods and technologies help narrowing the attack surfaces you make available to the threat actors.
Exposing your company’s assets is a necessity to maintain business relevancy. We must be able to communicate via email. We must interact with partners and suppliers by doing some sort of IT integration to be able to exchange information. We must be able to connect to the internet to ensure productivity.
So, what can we do to harden our companies to a degree where we can withstand attacks from these harmful organizations while still maintaining momentum and growth for our business?
One of the answers is segmentation.
Traditional Networks
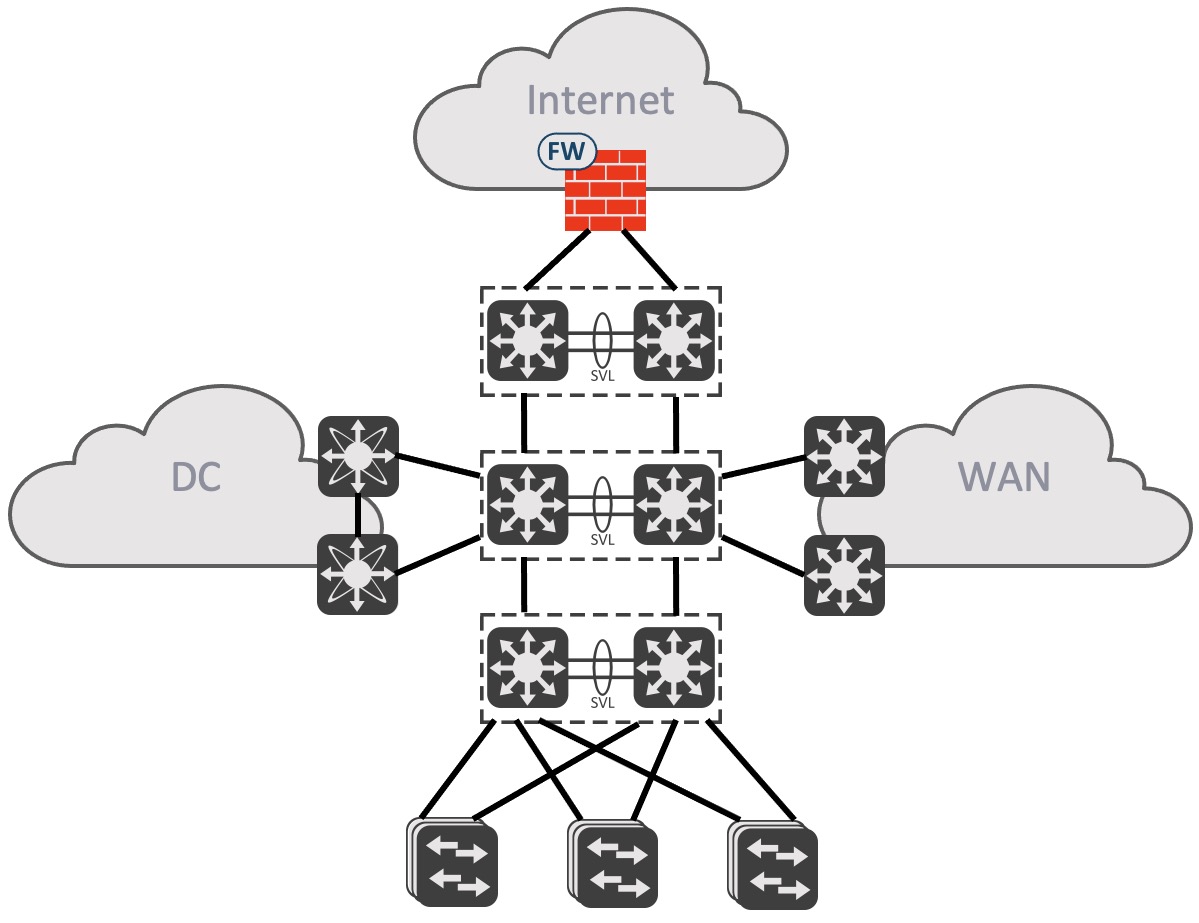
Below is a topology that overall accounts for what many companies have done. It is a classical traditional network with a core in the middle to inter-connect various modules or functions in the network. Like the Data Center, Internet edge, WAN, and Campus in the bottom. Notice the placement of the firewall. It is protecting only communications to and from the Internet.
From a functional point of view this works just fine and has for many many years. This fundamental way of building networks probably won’t change in near future. But from a security perspective, everything inside the company is at risk, because there are no measures to safeguard against malware outbreaks.
The traditional way of segmenting a network is through IP subnets and VLANs. Connectivity and network stability has always had focus over security.
Segmentation Today
Today we segment with security in mind. The key to maintaining good security practices is to keep software updated (patch management), train users (avoid phishing), and limit the attack surface. The latter is what segmentation is all about. Of course security is a lot broader than just these three things. If you want to dig deeper into security practices, CISSP might be a good place to look.
Below is an image that illustrates a high-level way to implement segmentation in the campus part of the network. Mind that segmentation in other parts of the network calls for different approaches and possibly other technologies to be implemented.
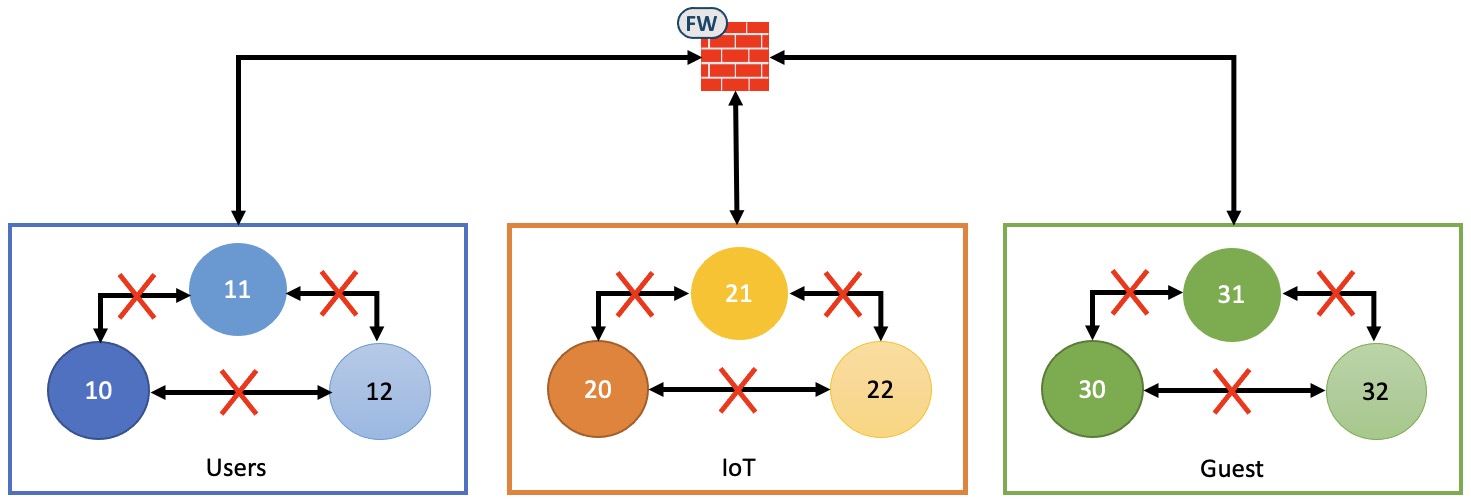
The squares could represent business units or larger grouping of the endpoints that connect to the campus network. We call them virtual networks, or VNs. Within each VN the circles represent groups of endpoints at an underlying level. We call them scalable groups, or SGTs.
The policy shown above is centered around a zero-trust model - or “allow-list” model - where communication can happen only if a contract allows it. We could also address this as a default deny method.
Only one SGT is required per VN. In the Users VN we might not need groupings of our internal users. Hence, we only need one scalable group for them to implement a restrictive policy:
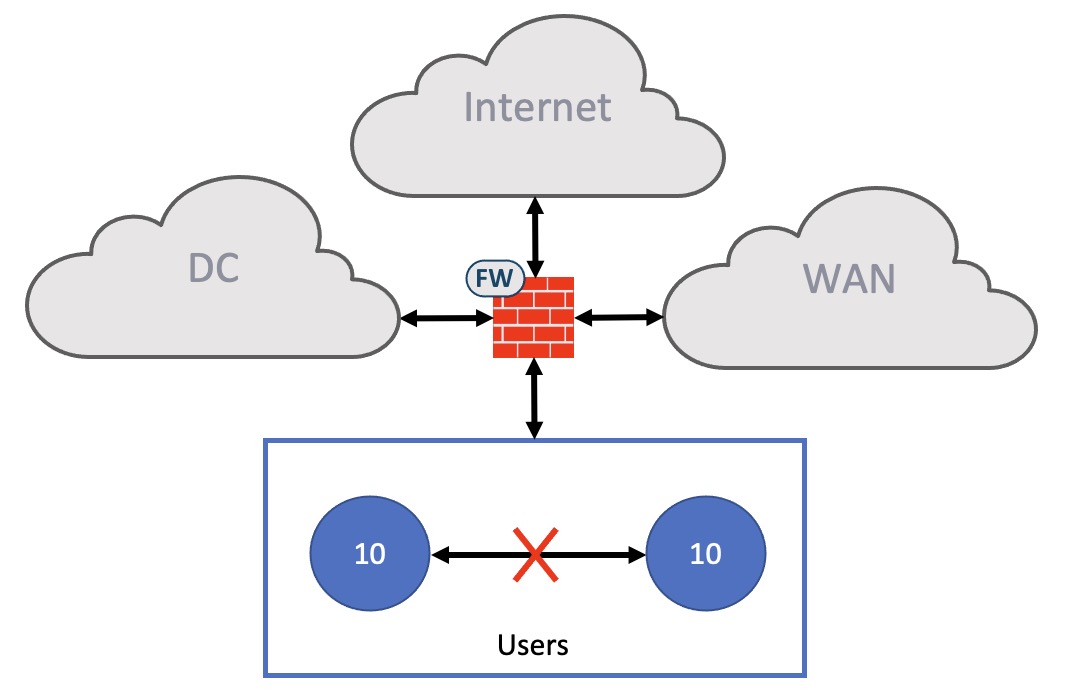
Here all users receive a SGT of numeric value “10”. Any users who receives this SGT will, be default, not be able to communicate with other users who also have the same SGT value of “10”. If you think about it, users do not require to be able to reach other users. General needs for communication between users typically happens via email, chat, or virtual meetings. All happen via servers in our data center or services in the cloud. There must be a specific reason, almost corner case, to define policies for allowing communications within the Users VN.
The IoT, or “things” VN, is another story. Here we typically have building management systems that require communication between them. And that’s OK! We can allow this via contracts by defining multiple SGTs - one per function that requires direct communication.
Whenever we communicate either between VNs (not recommended) or to other parts of the network or even the Internet, we should go through a firewall. Going through a firewall provides great benefits:
- Network-based malware protection (AMP)
- Protection against infected files as they’re sent through the firewall
- Intrusion Prevention System (IPS)
- Deep inspection of network and application traffic
- Application visibility and control
- Ability to allow chat, but block file transfers via chat, for example
- Reputation-based filtering
- Block bad web sites
- Guaranteed logging
Segmentation using VNs is called macro segmentation and segmentation using SGTs is called micro segmentation when we’re focussing on the campus part of the network.
Identity Management and Automated Configuration
Ensuring the correct endpoints (users, printers, video cameras) are onboarded to the correct VN with their group association using the SGT value, we somehow must identify each endpoint to the network. Cisco ISE can act as a policy engine that ensures only authenticated endpoints are allowed on to the network. We call this process endpoint onboarding. ISE will send an access-accept along with the values required to let the network switch know to which segment the endpoint is authorized to access (VN + SGT). Endpoints without valid credentials will not gain network access and ISE will send an access-reject to inform the network not to allow the connection. Alternatively we can have ISE allow the endpoint to enter a dedicated VN (like Guest) for this unidentified endpoint.
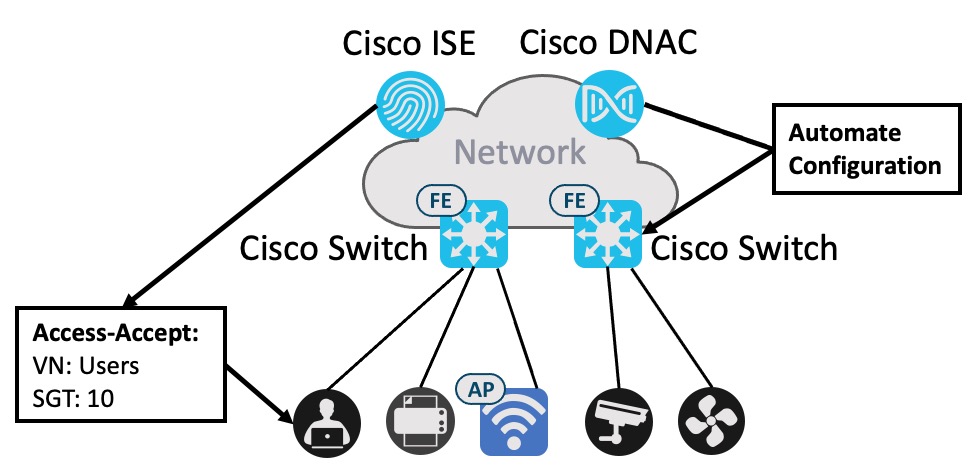
The communication between the endpoint and Cisco ISE is facilitated via the network switches. In fact, the switch will just relay the identity information received from the endpoint and ISE will send the authorization result to the switch that dynamically configures the port based on the values in the result (VN+SGT).
This dynamic behaviour makes it possible to configure all ports on all switches in a uniform way. Now you can move stuff around the network and connect it anywhere and the network will adapt and provide the configuration necessary for your required access level. IT operations will be freed of a huge burden of managing switch port configurations when people move offices, rooms are re-purposed to other functions like new meeting rooms and so on.
If we talk about Cisco DNA Center (DNAC) in combination with Cisco ISE, we can take this to the next level with automated deployment of switch configurations and software management of switches to name a few of its capabilities. Remember patch management is of great importance in keeping our infrastructure secure and stable.
With Cisco ISE and Cisco DNAC not only do we get the ability to implement a secure network using automation, we also gain visibility into which endpoints are connected to the network which is another critical aspect of security. If we don’t know what’s on the network, we cannot protect it.
Using these techniques in a modern network would be a great starting point to become more secure. Mind though, that no one solution or product alone can make your infrastructure secure. It is paramount that you invest in multiple solutions to address different risks of attack. This approach is called defense-in-depth. I am not a sales person, and I strongly believe in only doing what makes sense for the company I consult. You should not go out and buy products from all shelves a security vendor offers. Note that you not only need to pay for the products, but also be able to implement and operate them. They should help drive the business by keeping it secure rather than be an obstacle for your business operations due to lack of capacity to maintain the security solutions you bought. And never ever talk about specific products without first addressing and clarifying the actual needs of functionality in relation to your company. Having a well-defined security policy is crucial to be able to assess how to protect the organization from threats.
Processes and Responsibility
To be successful with security segmentation of any kind, a process needs to be in place. Segmentation is not something you implement once and you’re done and secure for good. Businesses change constantly with new services and business units being established which must be addressed and handled continuously. Most companies have well-defined ways of dealing with changes using elements of the ITIL framework for change management. Dealing with segmentation could be added to this process. The important part of defining policies and approving their implementation has to do with responsibility. Somebody must provide the actual need and requirements of the communication to justify the policy. And someone must review and approve the request before it can be implemented. It doesn’t have to be bureaucratic, but a process has to be used to keep track of changes and being able to justify the policies in place. Also, this will help when reviewing existing policies to help cleaning up obsolete policies when services or business units are torn down.
To enhance your cybersecurity resiliency, the CISO should report directly to the CEO. This will provide the necessary authority for the CISO to influence security decisions. You can’t ask someone to be in charge of security for your business and then put handcuffs on them. For sure they will be blamed when a security incident affects the business.
Audit
Taking responsibility for security is something to be proud of. You should demonstrate that you are in control and compliant with your security policy by doing a yearly security audit. This will highlight areas of your infrastructure that needs attention and it will show the overall maturity of your infrastructure in regards to security.
I recommend using CIS18 to make this compliance audit.
Conclusion
It is crucial to be serious about security in today’s IT infrastructure. To deal with the increasing risk level we must go with a defense-in-depth approach to limit the attack surfaces our companies are exposed to. In the campus network we can implement segmentation at the macro level using VNs and micro level using SGTs. This prevents users from being able to communicate directly with each other. A firewall should be used between parts of our network to look deeper into the traffic that should be allowed to conduct business.
A well-defined security policy should be in place in any company and the correct organization and processes should be in place to support this security policy.
To find and address shortcomings of our infrastructure, regular audits should be used. I recommend looking into CIS18 for compliance audits.
I hope you found this post useful.
