FlexVPN with AnyConnect-EAP using ISE and ZBFW
So you might have stumbled upon the FlexVPN: AnyConnect IKEv2 Remote Access with AnyConnect-EAP configuration guide which works OK for local user authentication and authorization. But if you try to follow the guide on how to configure authentication and authorization with a AAA server, it will not work!
This post addresses the configuration of using AnyConnect IKEv2 for a IOS headend using ISE as AAA server for authentication and authorization.
IOS XE Configuration
First off let’s define our AAA settings:
aaa new-model
!
aaa authentication login a-eap-authen group ISE
aaa authorization network a-eap-author local
aaa accounting network a-eap-acc start-stop group ISE
!
radius server ISE_Server1
address ipv4 172.16.12.3 auth-port 1812 acct-port 1813
key 0 MyS3cr3T!K3Y
!
aaa group server radius ISE
server name ISE_Server1
Next we need an ip pool:
ip local pool vpnpool 10.255.255.1 10.255.255.254
[]1Presenting a certificate for the client is mandatory with IKEv2. I’ll create a self-signed certificate for this setup:
crypto key generate rsa modulus 4096 label AnyConnect
!
crypto pki trustpoint TP_AnyConnect
enrollment selfsigned
usage ike
serial-number none
fqdn hostname.domain.private
ip-address none
subject-name cn=hostname.domain.private
subject-alt-name hostname.domain.private
revocation-check none
rsakeypair AnyConnect
hash sha1
!
crypto pki enroll TP_AnyConnect
Now to the “funny” part. We need a local dummy authorization policy config for the IKEv2 profile:
crypto ikev2 authorization policy ikev2-auth-policy
Nothing needs to be configured under this ikev2 authorization policy, BUT it MUST be configured! If you want, you can configure local attributes here, but if you have the same attributes configured on ISE, these will take preference.
The dummy policy is referenced by the following ikev2 profile:
crypto ikev2 profile AnyConnect-EAP
match identity remote key-id $AnyConnectClient$
authentication local rsa-sig
authentication remote anyconnect-eap aggregate
pki trustpoint TP_AC
dpd 60 2 on-demand
aaa authentication anyconnect-eap a-eap-authen
aaa authorization group anyconnect-eap list a-eap-author ikev2-auth-policy
aaa authorization user anyconnect-eap cached
aaa accounting anyconnect-eap a-eap-acc
virtual-template 100
I’m using the default IKEv2 proposal:
IKEv2 proposal: default
Encryption : AES-CBC-256
Integrity : SHA384
PRF : SHA384
DH Group : DH_GROUP_384_ECP/Group 20
We must disable certificate lookup based on HTTP URL:
no crypto ikev2 http-url cert
Now define the encryption and hash algorithms for protecting the traffic:
crypto ipsec transform-set TS esp-aes 256 esp-sha256-hmac
mode tunnel
Tie the transform-set with the ikev2 profile together with an IPsec profile:
crypto ipsec profile AnyConnect-EAP
set transform-set TS
set ikev2-profile AnyConnect-EAP
The final piece of configuration on the router is the virtual-template interface.
This interface is actually used as a template for creating a Virtual-Access interface when a user logs on. Here is an example:
interface Virtual-Template100 type tunnel
ip unnumbered Loopback0
tunnel mode ipsec ipv4
tunnel protection ipsec profile AnyConnect-EAP
That’s it for the router configuration! The AnyConnect client must also be configured.
AnyConnect Profile Settings
As there is no support for downloading the client settings with an IOS headend, we must tell AnyConnect to bypass the downloader. The file you’re looking for is called AnyConnectLocalPolicy.xml
Specifically this line is required:
<BypassDownloader>false</BypassDownloader>
Also you’re required to generate an XML profile for the IOS headend. Below is a sample. The important part of the XML file is the
ISE
In ISE we can create an authorization policy with these conditions:
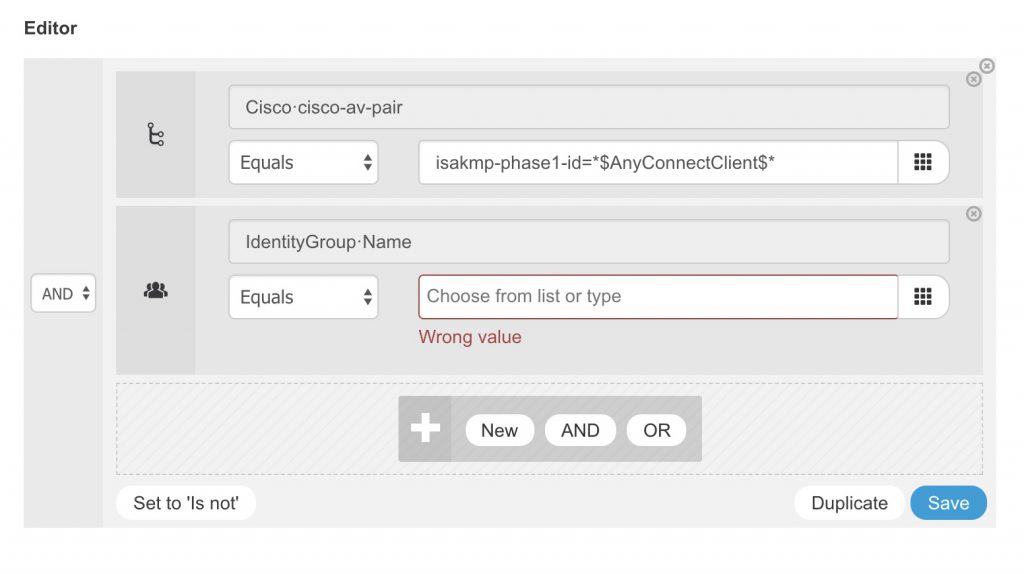
And we can create an authorization result that sends the needed VSAs. Here is an example:
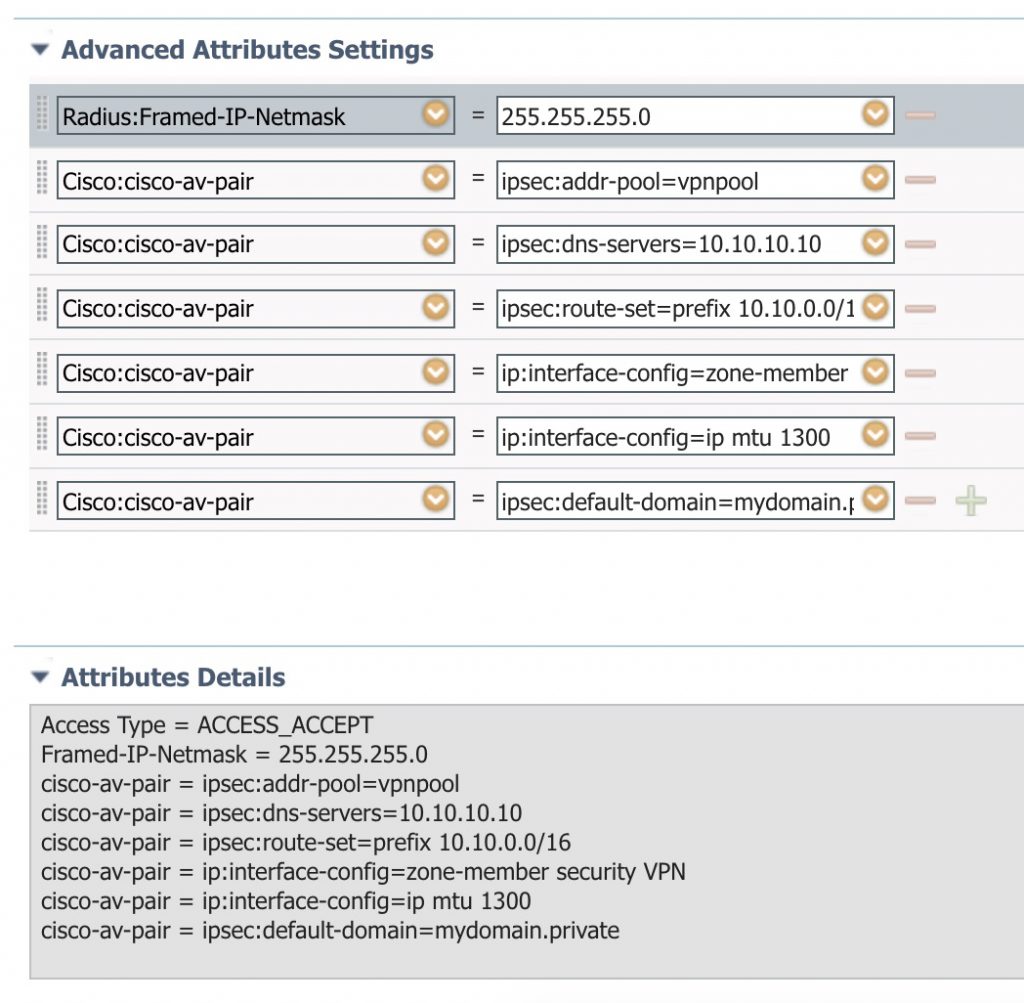
Verification
When you’re connected, you can verify the connection:
hostname#sh crypto ikev2 session detail
IPv4 Crypto IKEv2 Session
Session-id:52, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote fvrf/ivrf Status
1 1.2.3.4/4500 4.3.2.1/52335 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA384, Hash: SHA384, DH Grp:20, Auth sign: RSA, Auth verify: AnyConnect-EAP
Life/Active Time: 86400/53 sec
CE id: 1566, Session-id: 52
Status Description: Negotiation done
Local spi: 11B77075D4D6E532 Remote spi: BCA5412A6F605ABF
Local id: 1.2.3.4
Remote id: $AnyConnectClient$
Remote EAP id: username
Local req msg id: 0 Remote req msg id: 6
Local next msg id: 0 Remote next msg id: 6
Local req queued: 0 Remote req queued: 6
Local window: 5 Remote window: 1
DPD configured for 60 seconds, retry 2
IETF Std Fragmentation configured.
Dynamic Route Update: disabled
Extended Authentication not configured.
NAT-T is detected outside
Cisco Trust Security SGT is disabled
Assigned host addr: 10.255.255.9
Initiator of SA : No
Child sa: local selector 0.0.0.0/0 - 255.255.255.255/65535
remote selector 10.255.255.9/0 - 10.255.255.9/65535
ESP spi in/out: 0x9D33D864/0xC858224A
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-CBC, keysize: 256, esp_hmac: SHA256
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
hostname#sh crypto session detail
Interface: Virtual-Access1
Profile: AnyConnect-EAP
Uptime: 00:08:26
Session status: UP-ACTIVE
Peer: 4.3.2.1 port 61831 fvrf: (none) ivrf: (none)
Phase1_id: $AnyConnectClient$
Desc: (none)
Session ID: 8
IKEv2 SA: local 1.2.3.4/4500 remote 4.3.2.1/61831 Active
Capabilities:DFN connid:3 lifetime:23:51:34
IPSEC FLOW: permit ip 0.0.0.0/0.0.0.0 host 10.255.255.9
Active SAs: 2, origin: crypto map
Inbound: #pkts dec'ed 355 drop 0 life (KB/Sec) 4607958/3094
Outbound: #pkts enc'ed 0 drop 0 life (KB/Sec) 4608000/3094
And for the final verification that our settings did actually get applied to the newly created Virtual-Access interface:
hostname# sh derived-config int Virtual-Access1
interface Virtual-Access1
ip unnumbered Loopback0
ip mtu 1300
zone-member security VPN
tunnel source 1.2.3.4
tunnel mode ipsec ipv4
tunnel destination 4.3.2.1
tunnel protection ipsec profile AnyConnect-EAP
no tunnel protection ipsec initiate
Troubleshooting
To debug the IKEv2 stuff:
debug crypto ikev2
debug crypto ikev2 packet
debug crypto ikev2 internal
debug crypto ikev2 error
A bit more relevant is to debug AAA stuff. This also verifies that we’re receiving the correct attributes from ISE and that we do not get any errors.
debug aaa authorization
debug aaa authentication
debug radius authentication
To see a list of supported attributes visit FlexVPN RADIUS Attributes
